The Y-Station
Introduction
Before decrypting Enigma messages, you must recover them. That was the goal of Y stations.
German army units communicated with each other in Morse code by radio (also called W/T: Wireless Telegraph) or telegraph line. Only stations in the same radio network on a specific radio frequency could communicate with each other. Each station was identified by a “call-sign” (e.g., N7Y or RNC). When it transmits a message, a station indicates its call-sign and that of its correspondent. A special call-sign indicated that the message was intended for all stations (broadcast). For security reasons, call-signs and radio frequencies were changed daily. If a station wanted to communicate with a station belonging to another radio network, it had to indicate this by specifying an intermediate station (part of the two networks) which served as a relay (Welchman 1998; Calvocoressi 2001).
An Enigma network, for example, that of the army, was made up of a certain number of stations (each corresponding to an army corps, a division,etc.), communicating with each other in encrypted form via the Enigma and using the same key table (Schlusseltafel). An Enigma network could correspond to a radio network but does not have to. Certain radio stations could belong to several radio networks and could, thus, allow communication between two stations of the same Enigma network belonging to different radio networks.
Radio links could be intercepted by the enemy. In England, interception stations were called Y-stations. These stations did not only intercept messages; they also produced intelligence. In particular, thanks to direction finding (D/F), they could locate German stations geographically (within 30 miles) and, in some cases, identify German radio operators via their “chat” and “fists” (the way of transmitting Morse code which is specific to each operator, similar to handwriting which is specific to each writer). On the other hand, the most active unit would be the HQ (Head Quarter).
Example: The interception of a message
For each intercepted message, the operator fills out a form:
Ref. No: 1 Page: 1 Ship or Station (Y station): ZER Set (Radio Set): F1 Opr. (Operator): John Doe To (Call-sign): APY From (Call-sign): 6QG Frequency (Kcs) & System: 1475 Date: 02-14-41 Time ended (GMT): 12:30 Operator’s remark (quality of reception?): O.S.A: 4/5 All before the text (Header): 1200 31 =ROM= =LNS= Text (Cryptogram): QKNVT WCGLV EUTCF ZTQSA WJCSR FQOOZ Z
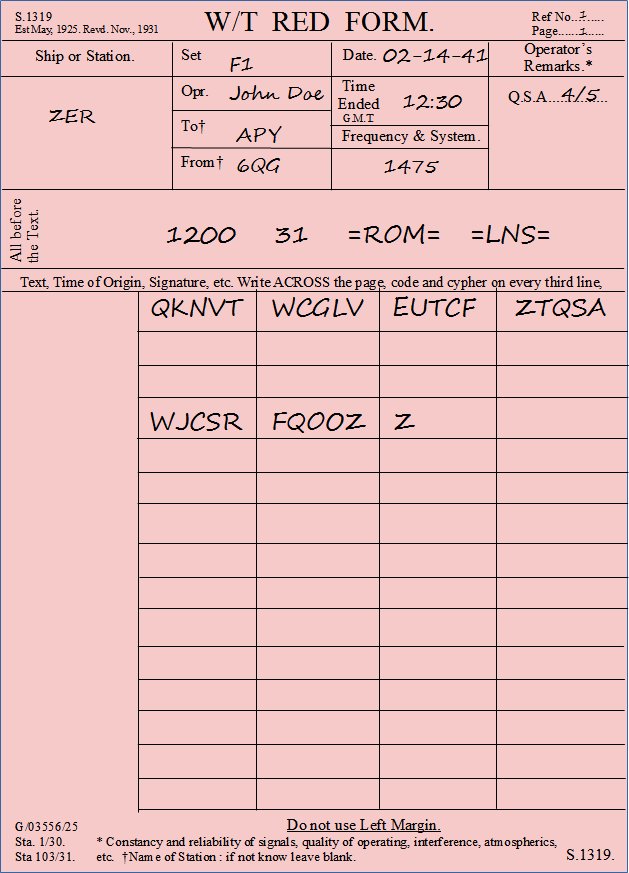
These forms are then sent to BP by motorcycle and/or by teleprinter. In this case the most important information is transmitted:
ZER/1. 6QG APY 1475 Kcs 1200 31 =ROM= =LNS= QKNVT WCGLV EUTCF ZTQSA WJCSR FQOOZ Z
Informations about radio and Enigma networks
In addition to the interception of messages, the Y stations send to BP information concerning enemy radio networks, coming from the messages (call-sign, frequency, ...), from the volume of traffic, or from the direction finding (D / F)
Example:
Several messages were intercepted. The messages have been sorted by frequency and D/F. Some operators have recognized the fist of enemy operators and have thus been able to confirm the location of several stations.
1st network:
- Frequency: 950 Kcs,
- Call-sign of the stations:
- Berlin: SAD (central station)
- Tripoli: 9HD
- Alle (broadcast): TN3
2nd network:
- Frequency: 1475 Kcs
- Call-signs of the stations:
- Berrlin: APY (central station)
- Dunkirk: 6QG
- Alle (broadcast): N7Y