The great crisis (May 1940- August 1940)
Introduction
At the beginning of May 1940, the Germans changed their procedures and Zygalski's sheets were no longer usable. For 20 days, it's a complete blackout. Then the decipherments are resumed using manual methods: the cillies and the Herivel tip.
The war
The procedural change in the use of the Enigma by the Germans shelters Zygalski's sheets and covers the Battle of France. This battle corresponds to the invasion by German troops of France but also of Belgium and the Netherlands, making a turning point after a breakthrough in the Ardennes. This, because of the terrain, had been deemed unthinkable by the French state major. After having cut the French army in two, the German army surrounds part of it as well as the English troops in the pocket of Dunkirk. The English manage to re-embark. Afterwards the German troops turned on the remaining French forces and in a few weeks defeated them. France surrendered in June 1940, leaving England alone to face the Axis troops.
After a brief respite, Germany attacks England from the air: the Battle of Britain begins.
The keys
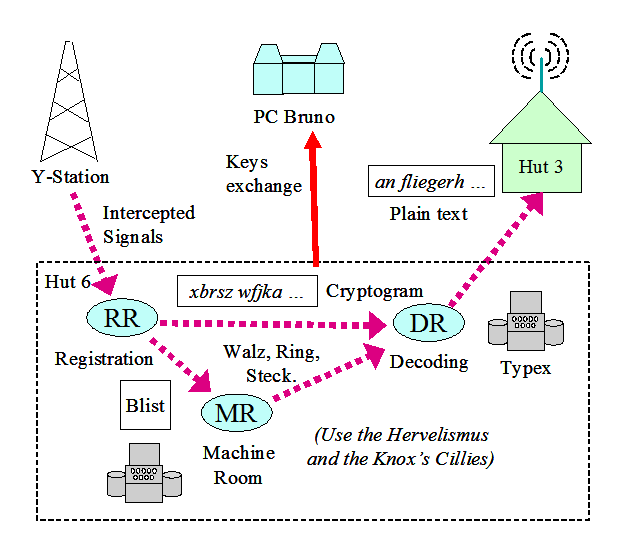
During the previous period, Hut 6 deciphers four networks (keys) identified by colors:
- Red: the air force (the luft)
- Green: the army
- Blue: an Air Force training network.
- Yellow: an air force-army combined force for Norvegian Campaign
Welchman suggests that the CG&CS leadership should focus only on the red network because of its quality in terms of information, but also because Hut 6 cannot afford to break as many keys as before. It must also be recognized that the red network respects the safety instructions less and is easier to break. His proposal is accepted and thus only the Red network will be attacked.
The organization
It's almost the same as before:
- The RR takes care of receiving the cryptograms and their header and classifying them (network, etc.).
- The DR takes care of the decryption of messages when the keys are found.
The MR takes care of finding the keys using manual methods: Knox's cillies and Herivel's tip.