M-209 - Genuine messages
Introduction
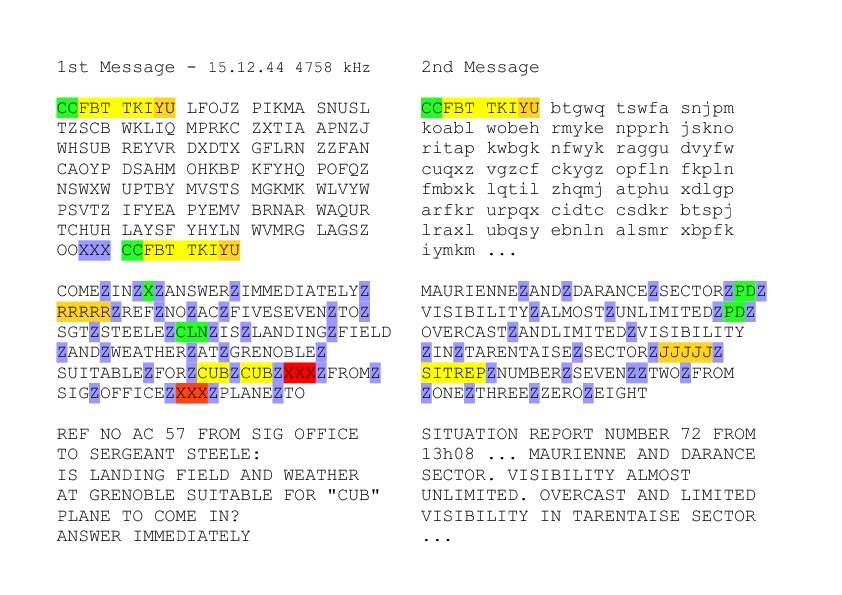
In TICOM archives (DF-120) we can find two authentic messages encrypted with the machine M-209.They come from the region of Grenoble in France in late 1944 just before the Battle of the Bulge. The second message is incomplete.
In the above picture you can see the two messages. First there is the ciphertext, then the raw decryption and finally the plain text well shaped. This latter form does not appear in the TICOM document, it is a personal interpretation based on the explanations that can be read in the document.
Preparation of a message before ciphering
The TICOM document tells us how was prepared a text before encryption. It confirms the drafting practices described in various US manuals.
The spaces between words are replaced by the letter "Z". In deciphering mode, the M-209 cipher machine prints a space each time a "Z" appear.
Stereotyped beginnings are, of course, forbidden, and likewise the encipherment of nulls by "X" or "Z" at the end of the message.
The message is cut in the middle, even in the middle of a sentence. Then the two parts of the message are switched. The real beginning is made recognizable by the words MSG BGNS (message begins) or by five-fold repetition of one letter.
Addresses are principally given only somewhere in the middle of the message, inclose either in the abbreviations PAREN, CMA, PD, CLN or XXX.
Abbreviations:
- PAREN parenthesis ("(",")")
- CMA comma (",")
- PD period (".")
- CLN colon (":")
Maybe other abbreviations were used. They are not mentioned in the TICOM document but appear in another one (NTP 3) that lists the abbreviations allowed in an American military message. Here are the most likely:
- DASH Hyphen or dash ("-") [confirmed by TICOM I-175 document]
- QUES Question mark ("?")
- SLANT Slant ("/")
- QUOTE...UNQUOTE Quote ("'"..."'")
In the first message, The question mark wasn't indicated by the QUES expresion, but by a X.
In the document, the German cryptanalyst complained of the multitude of abbreviations used. Can be interpreted with a low error probablity those following:
- REF: Reference
- SIG: Signal
- SGT: Sergeant
- SITREP: Situation Report
I think the four digits following the word "FROM" correspond to a time, 01:08 here.
Remark: The word CUB is duplicated because it does not match an abbreviation but a proper name: the Piper Cub plane.
Preparation of the message after encryption
If the number of letters in the message is not a multiple of five, the message after encryption is completed by a series of character "X".
The two indicator groups are added before and after the cryptogram. The indicator of the message follows the usual rules well described by Mark J. Blair (NF6X): a duplicate letter followed by six letters that match the key used to generate the message key and finally two letters that specifies the network encryption.
Messages in depth
In fact, in the DF-120 document, the two messages appear in depth. Some characters are underlined. This indicates errors. I understood it after reconstituting the key and deciphering the cryptogram. At least the first two errors are probably Morse errors. There is an "S" (...) instead of a "I" (..) at position 7, and then a "Z" (- - ..) instead of a "G" (- - .) at position 17.
There is also a simple error: the cipher clerk has forgotten the letter "D" at the end of the word AND.
The key
Because the two messages are in depth, one can reconstruct the key.
Lugs: 1-6 2-0 2-0 3-5 0-4 0-6 1-6 2-0 2-0 3-5 0-5 0-6 2-0 2-0 2-3 3-0 0-5 2-0 2-0 2-3 3-0 0-6 2-0 2-0 2-3 3-0 0-6 Pins: Wheel 26: A___E_G_I_KL___P__ST_V_X__ Wheel 25: ABCD__GHIJ_L___P__STU__YZ Wheel 23: A_C__F_H___L_N__QR_T__X Wheel 21: AB_D_FG_IJ_LM_____S__ Wheel 19: _B___FGH__K___OPQRS Wheel 17: AB_____H__KLM_OPQ
There are seven Lugs overlaps. The 1944 TM 11-380 manual says that the number of overlaps must be between 1 and 12. For one wheel, there are six pins in effective position in a row. It is the maximum allowed. There are 50% of pins in effective position. 40% to 60% of pins must be in effective position. You can see that the 1944 manual rules of key creation are respected.
References
- "Report on the solution of messages in depth of the American cipher device M-209" TICOM DF-120.
- Report by Alfred Pokorn of OKH/CHI, on M-209. TICOM I-175.
- NAVAL TELECOMMUNICATIONS PROCEDURE TELECOMMUNICATIONS USERS MANUAL NTP 3 (J) NTP 3
- Converter M-209 B, Mark J. Blair, May 1 2009 NF6X
- War Department Technical Manual TM 11-380 M-209