|

|

|
History
B-21 and the Swedish Army
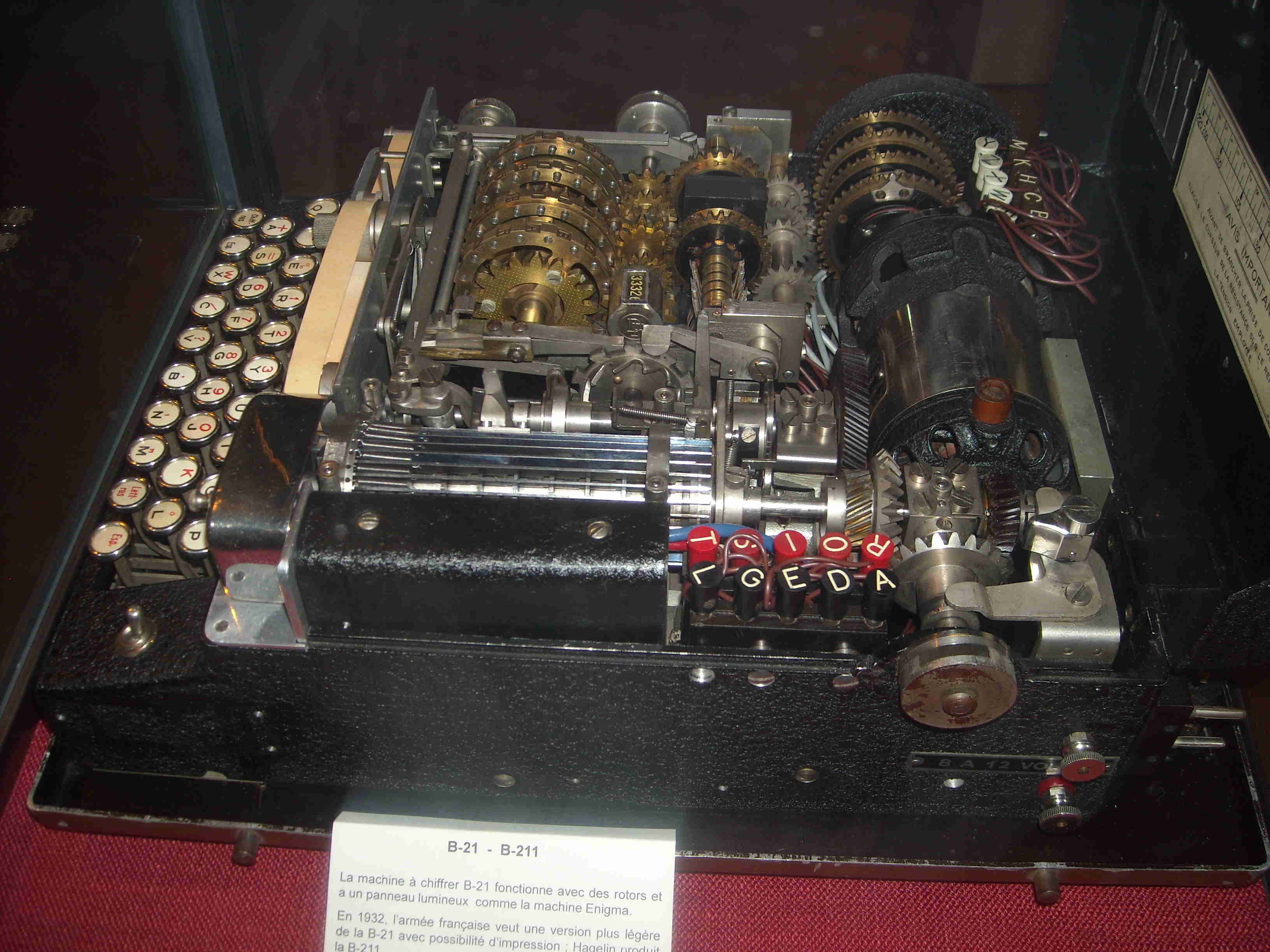
Cipher Machine B-21 was created by Boris Hagelin. This machine was designed in 1925 when Mr Hagelin learned that the Swedish army was ready to equip itself with Enigma machines. In less than six months he developed a machine that externally was like Enigma but in fact, was very different cryptographically. In particular he introduced wheels having "Pins" active or not that should be the main elements of machines of the series C in particular the M-209.B-211 and the French Army
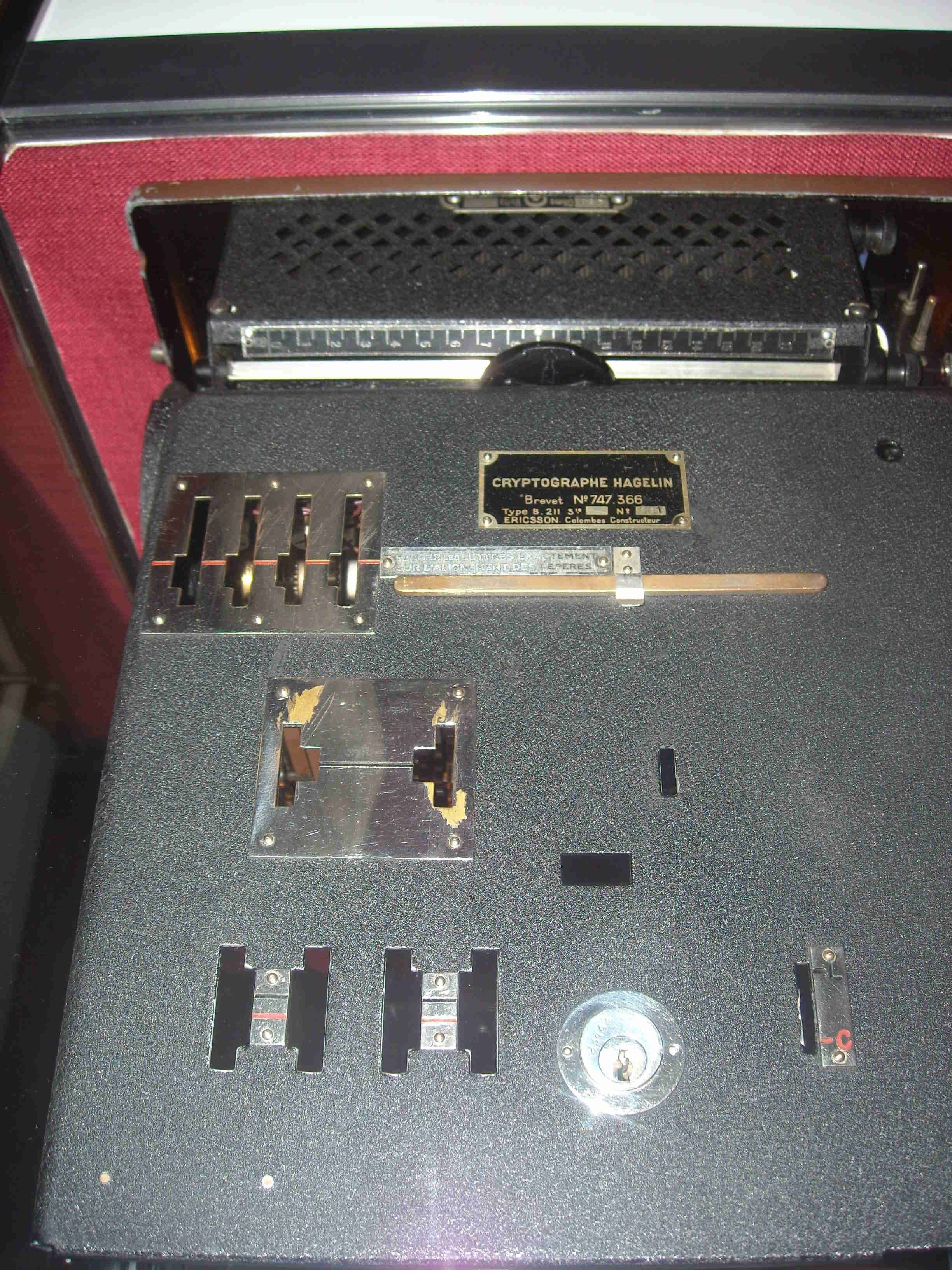
In the 1930s, Mr Hagelin made several trips to find new customers for his B-21 machine. The French army was interested but asked for changes: The machine must be able to print messages and be portable. The resulting Machine was named B-211. She could not just print all the letters but the numbers and several special characters (+, -,%, =, ...) too. A crank could operate the machine in abscence of electricity (usually a battery was scheduled to power the machine). Manufacturing was conducted in France near Paris by Ericsson. 500 machines were delivered in 1939 just before the beginning of the war.The French B-211 at the beginning of World War II
The B-211 was used at strategic level: corps and army. The Machine Hagelin C-36 was used at the tactical level: at Division level and below.The indicator system was complex but not very sure. It was the same method used to conceal the start wheel setting of C-36.
The Germans were not able to decipher the French messages (C-36 or B-211) during the phoney war. Actually, the traffic was low and the signal units used essentially wire lines.
After the collapse of France, the Germans could get a copy of the B-211. They studed their back log and found a method to read the accumulated messages.
The Soviet B-211
Mr Hagelin was forced by the Swedish authorities to sell B-211 to the Russian Embassy. Then Soviet copied this machine and they called it K-37 Crystal. The Germans never intercepted Soviet B-211 traffic but they captured one. In fact, B-211 was used in the Soviet Far East in 1945. It was intercepted and decrypted by the Americans. The traffic end in 1947.The B-211 Model two (M2)
In the middle of the war (1942/1943), the French improved the B-211 machine by adding an super-encryption equipment. This second model (M2) entered service in 1942 (or 1943). Neither the German nor the American could not break this new machine. This model brought a high level of security.After the war
After the war, the French continue to trust the B-211. Besides they bought additional 100 copies to compensate for lost or destroyed machines.The Franco-British intervention in Suez Canal in 1956 ended the use of B-211. The British said to French that the Americans could read B-211 encrypted messages. The B-211 was replaced by cipher machine KL-7 from NATO.
Working
B-21
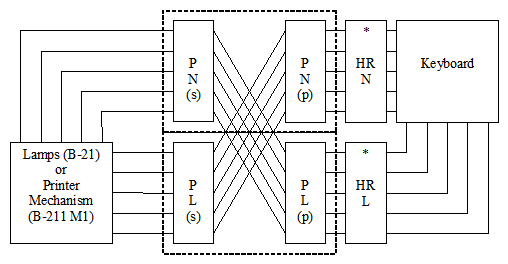
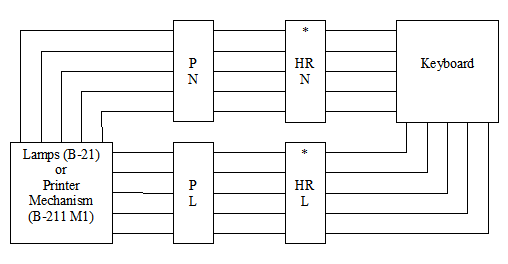
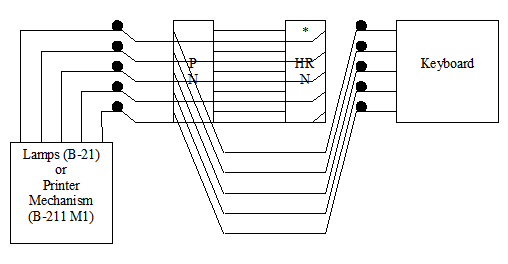
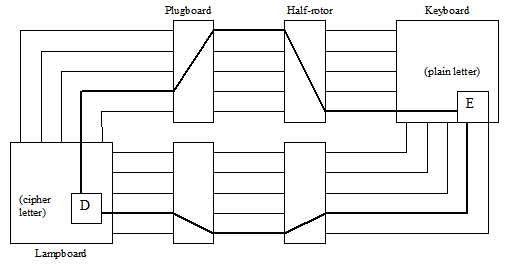
Each letter encrypted is fractionned in two signals by means of the keyboard. This keyboard is a 5x5 square (one low frequency letter K,J,W or Z is omitted). When you hit a key, two electric circuits are closed indicate the row and column of the square. Each channel (the row and column [also called numeral and letter, or vowel and consonent]) is ciphered separatly by means of an Half-rotor and a plugboard. Each device realises a permutation of the five electric circuits. Finally, a recombination of the two channels through another 5x5 square (a lampboard) gives the resultant letter (the encrypted or the decrypted one).Unlike the Enigma encryption and decryption are two different operations. You must configure the machine in encryption mode or decryption mode (electric cirtuits are then reversed).
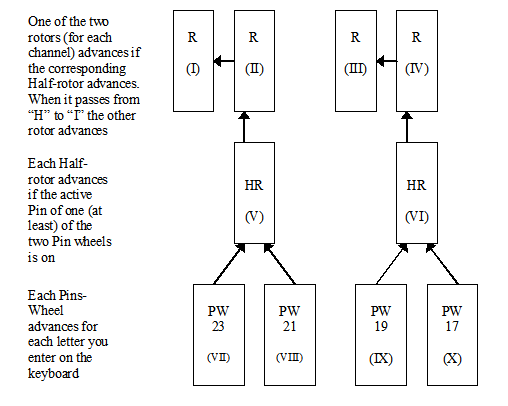
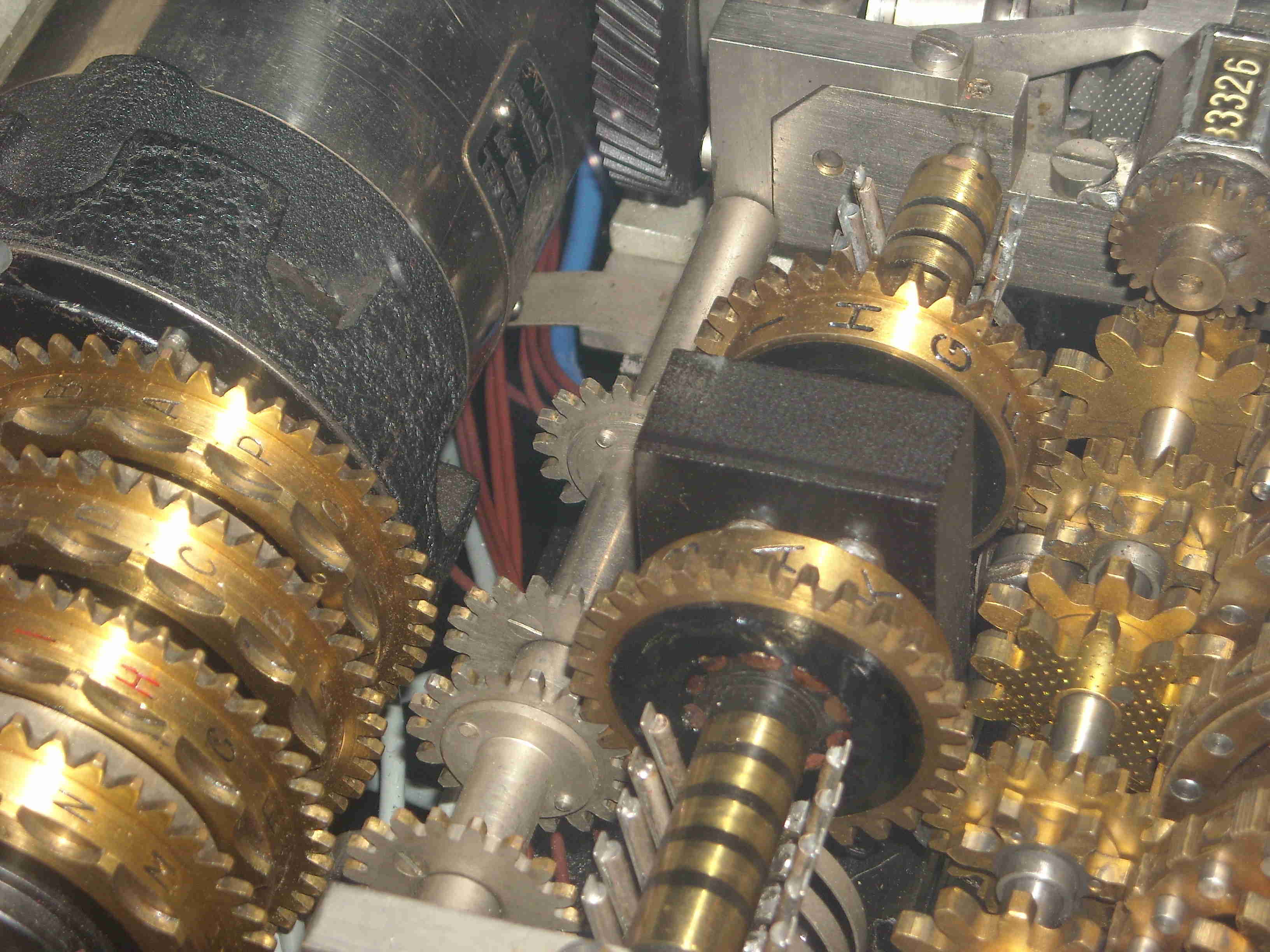
The Half-rotors can move (and then generate a new permutation) at each encrypted letter. One half-rotor advances if the active pin of one of the two Wheels which controls it is on. There are four Pins wheels. They advance one step at each keystroke. The wheels with 23 and 21 pins control the advancement of the first half-rotor, the wheels with 19 and 17 pins control the advancement of the second half-rotor.
The key:
- The basic key is composed by the keyboard fractionnement and the wiring of the two half-rotors.
- The internal key is composed by the setting of the two plugboards and the setting of the four wheels Pins.
- The external key is composed by the start position of the two half-rotors
a letter from 'A' to 'K' (ABCDEFGHIK) and
the initial position of the four Wheels Pins:
- Wheel 23 : a letter from the set : 'ABCDEFGHIKLMNOPQRSTUVXY'
- Wheel 21 : a letter from the set : 'ABCDEFGHIKLMNOPQRSTUV'
- Wheel 19 : a letter from the set : 'ABCDEFGHIKLMNOPQRST'
- Wheel 17 : a letter from the set : 'ABCDEFGHIKLMNOPQR'
Diagrams: The following diagrams show the electric path in the encipherment mode (left diagram) and in decipherment mode [only for numeral channel] (right digram). "HR N" means Half-rotor for the numeral channel. "HR L" means Half-rotor for the letter channel. "P N" means Numeral Plugboard and "P L" means Letter Plugboard.
 |
 |
 |
B-211 M1
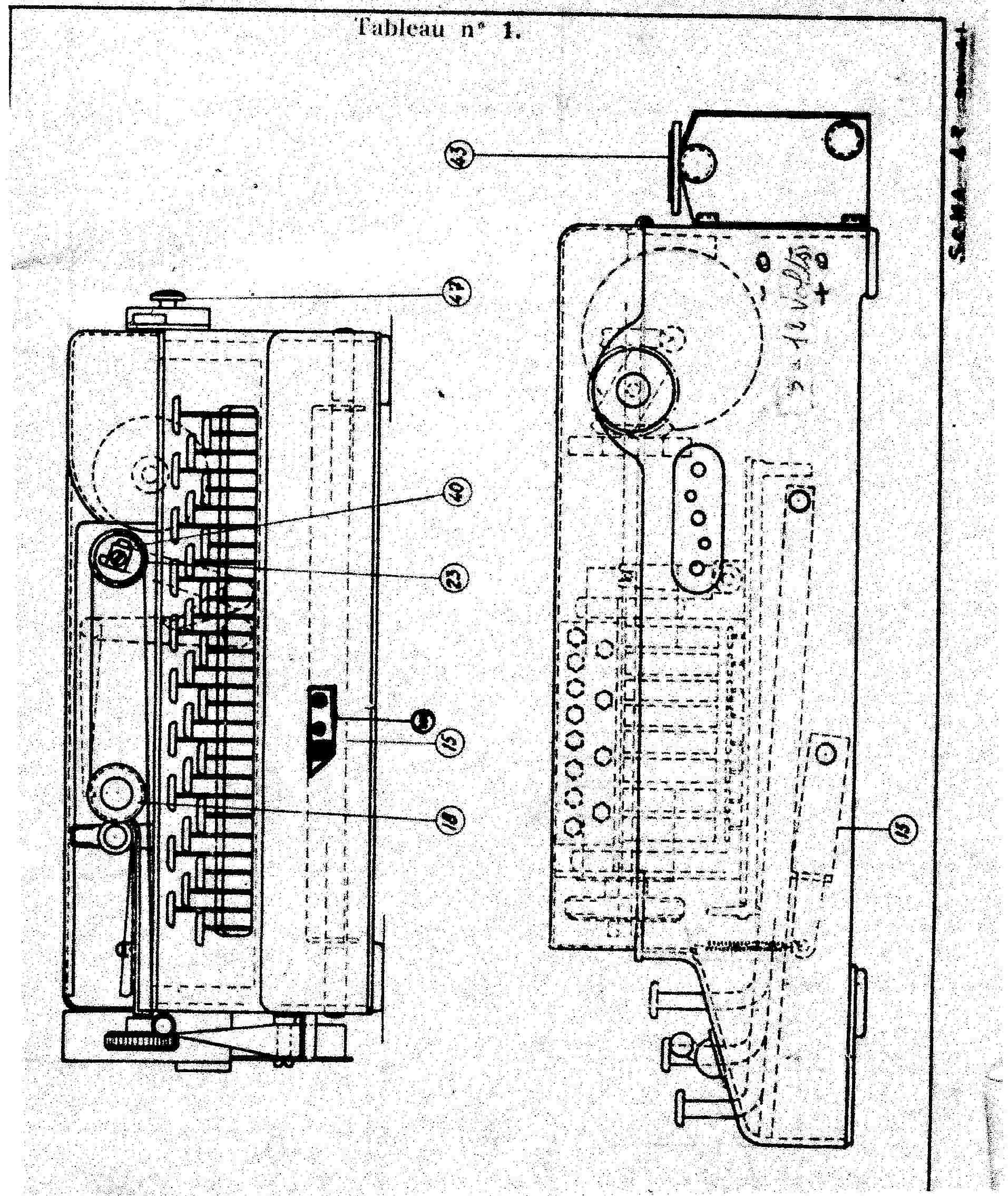
|
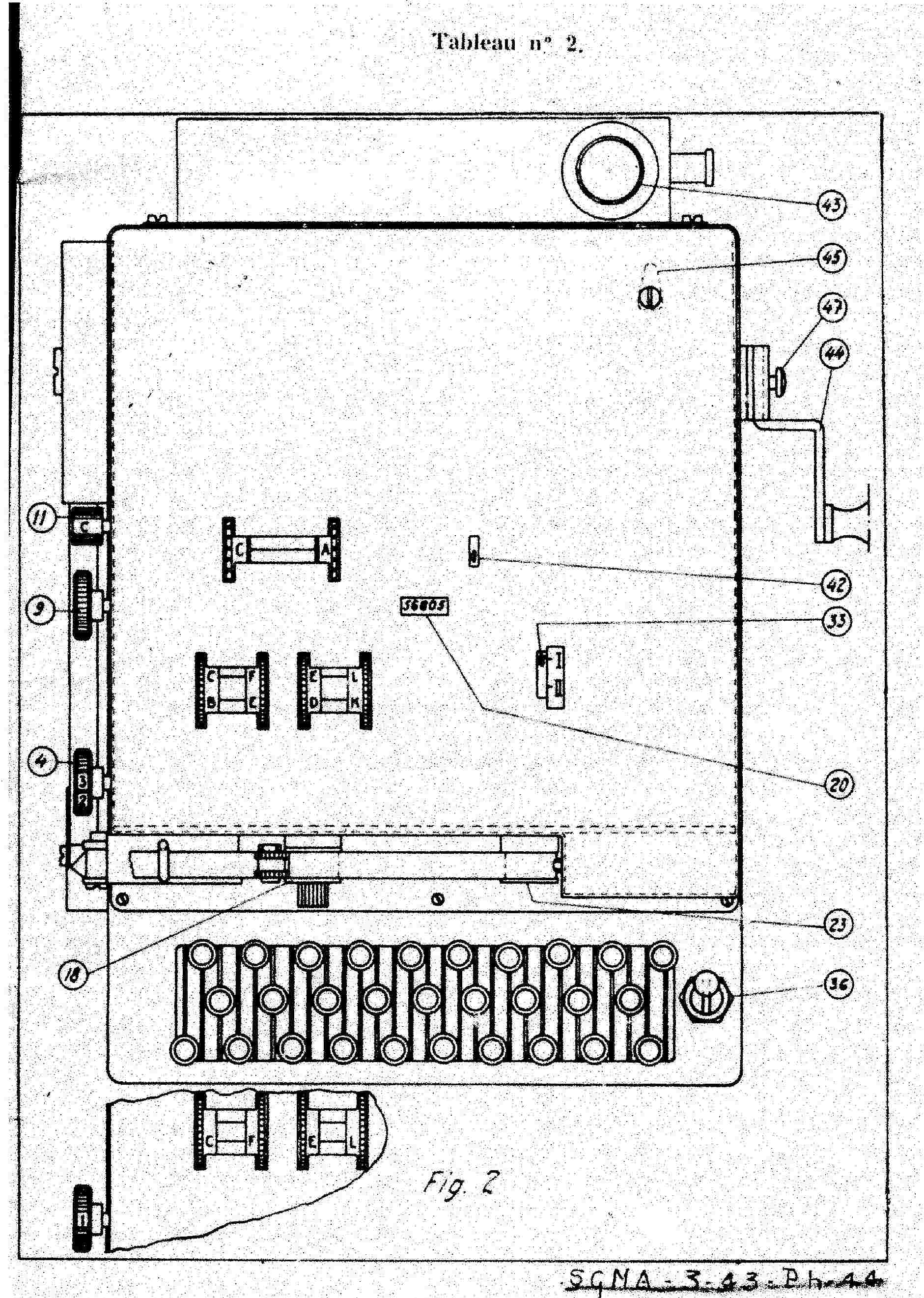
|
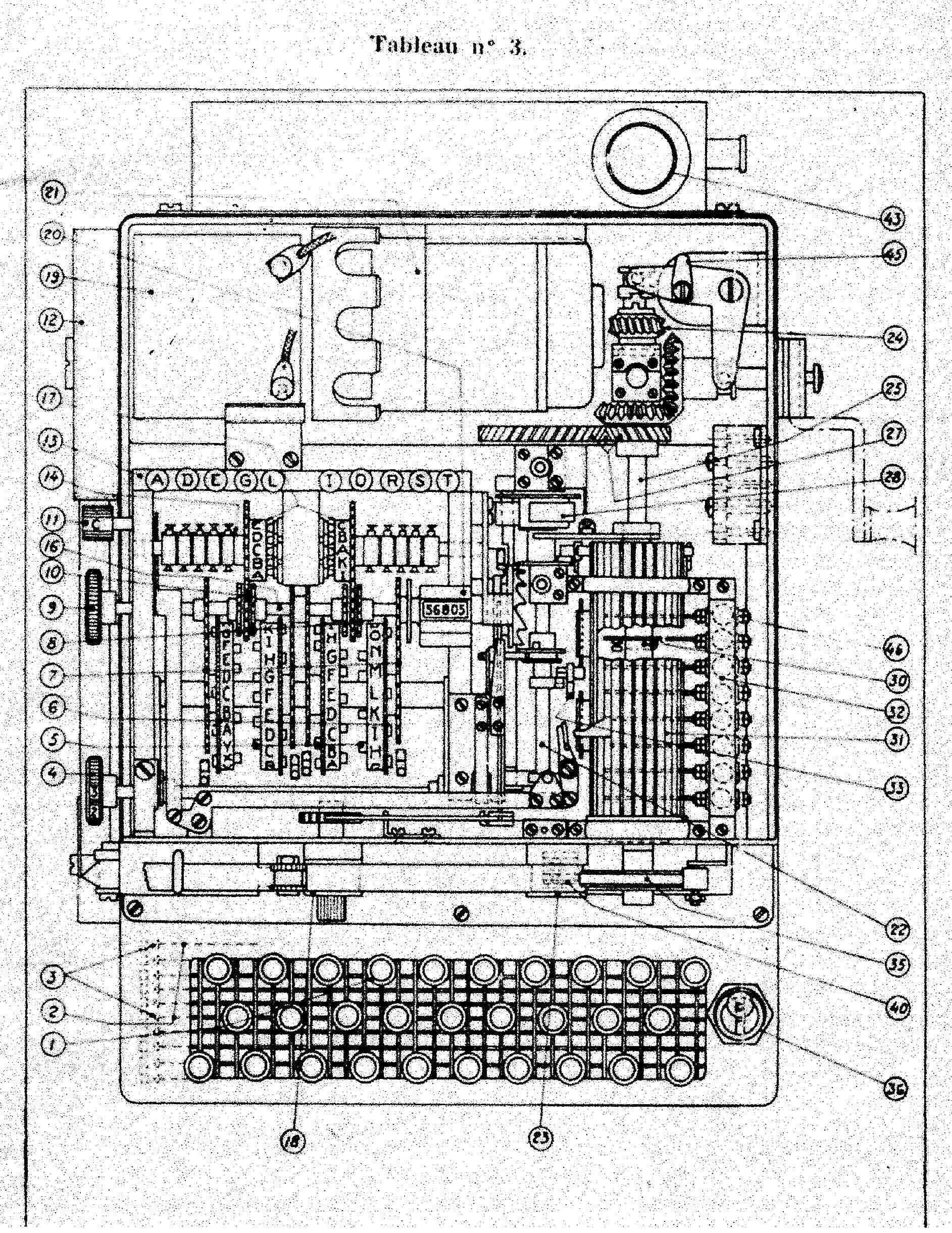
|
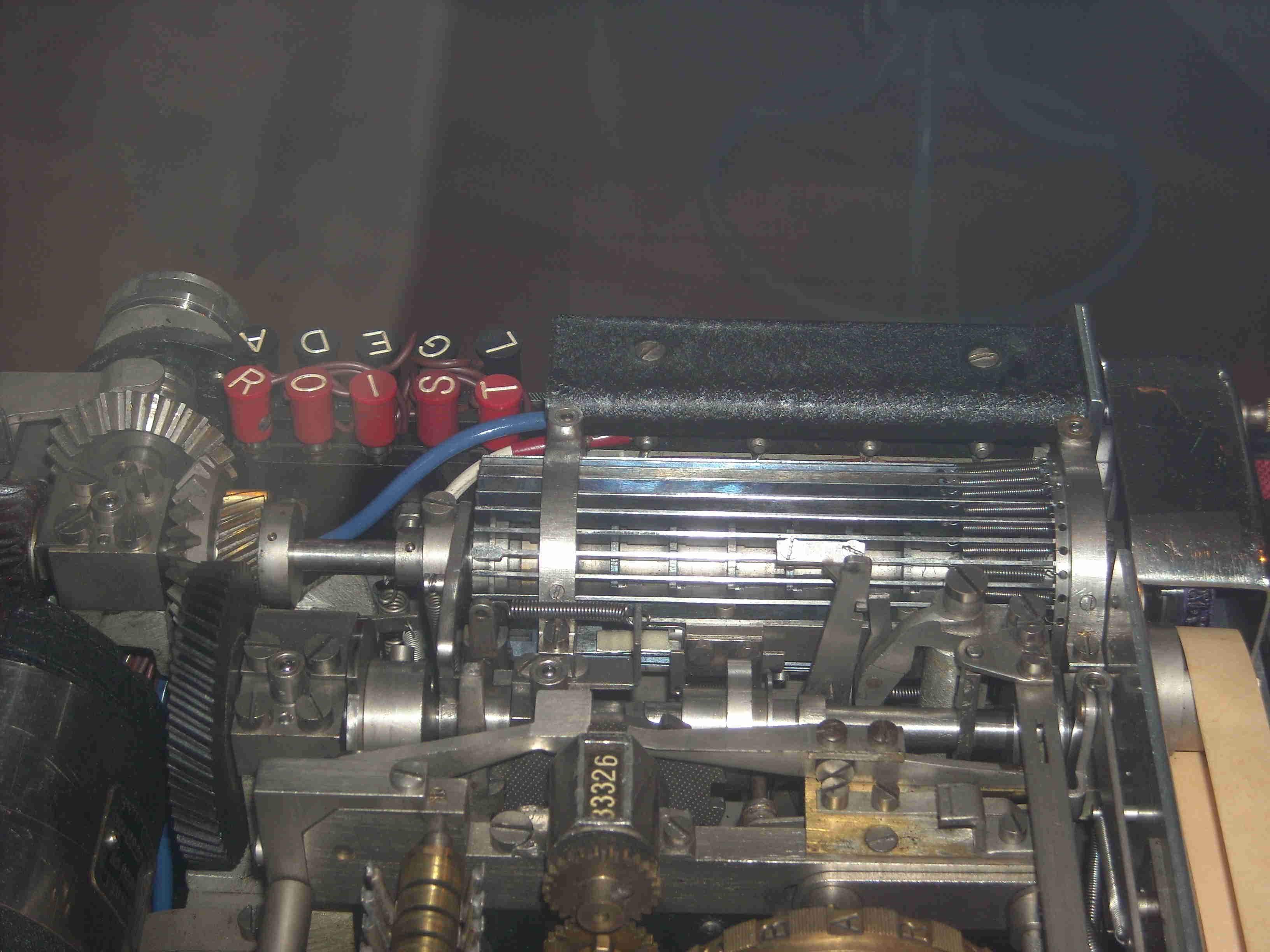
The working of the first model of B-211 is the same of B-21 one. The principal difference is the machine can print the ciphered (or deciphered) letter. A shift mechanism permits to print 48 characters. These characters are splited in two groups: the black signs (principaly the letters) and the red signs ( principaly the numbers). In each group, a key permits to switch to the other group: The black sign "Chiffre" and the red sign "Letter". Another peculiarity of B-211 is to act as a simple typewriter if you disable the cipher or decipher mechanism.
|
|
Finally, as both plugboards are close to each other, it is possible to cross both channels. Just connect the plugs of the one plugboard in the sockets of the another plugboard (see diagram below).
B-211 M2
The second model has a super-encipherment device (or super-encryption device). For each channel, the super-encipherment device consists of two rotors and a new plugboard. One rotor per channel advances when the corresponding half-rotor advances. When the fast rotor made a full turn, the other rotor steps.No official diagram describes the details of this super-encipherment device. A document from a French former cipher clerks association ([10]) shows the detail of the super-encipherment device. But I didn't agree with it. I got it reconstructed on the assumption that the second model must be configured to be compatible with the first model. That implies that plugs of the first plugboard must be inserted into the sockets of the second plugboard. Both rotors being then isolated from the encryption circuit.
In July 2016, I was very happy to discover a NSA document ([15]) which confirms my deductions. Then I can say that my B-211 simulator is correct not only to simulate M1 model but the M2 too.
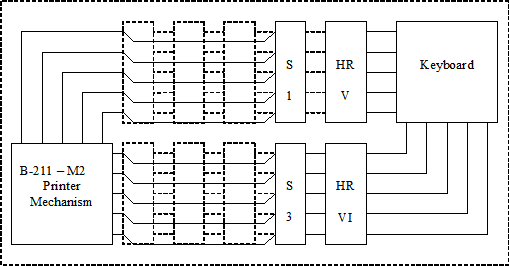
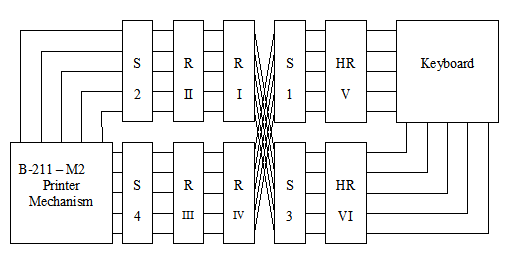
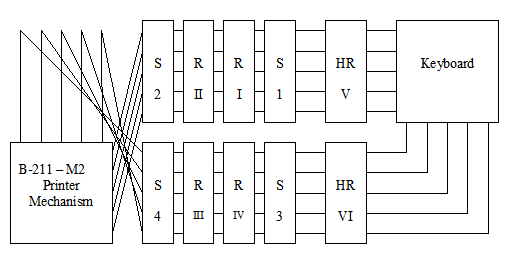
Diagrams (I use the NSA terminology): The first diagram shows the components of M2 model: The two Half-rotors (HR [V] and HR [VI]), the four plugboards (or steckers) [S1, S2, S3 and S4] and the four rotors (I, II, III, IV). The second diagram shows the M2 model in compatible mode with M1 (the super-encipherment device is skipped). The last diagram shows the advancement of Pins wheels (VII, VIII, IX, X), half-rotors (V, VI) and rotors (I, II, III, IV).
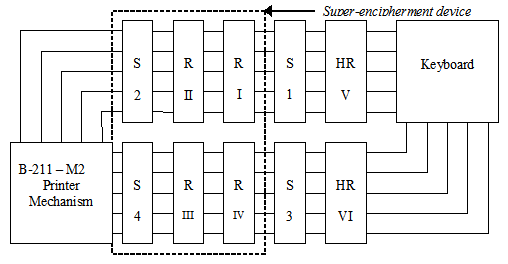 |
 |
|
The NSA document describes two cross-plugging configurations but don't talk about the compatible mode. In the first cross-plugging configuration, the plugs of the first plugboard of the numeral channel (S1) are plugged into the sockets of the first plugboard of the letter channel (S3) and vice versa. In the second cross-plugging configuration, the plugs of the second plugboard of the numeral channel (S2) (are plugged into the sockets of the seconf plugboard of the letter channel (S4) and vice versa. It is possible to apply the both cross-plugging settings, then we exchange the couple of rotors of the numeral channel with those of the letter channel.
Thanks to the NSA document, I also learned that (for each channel) the another rotor was not static, but it advances when the rapid rotor passes from "H" to "I". Note: The ARCSI document doesn't mention that.
 |
 |
The four rotors have each fifteen starting positions: 'ABCDEFGHIKLMNOP'. At each position, only 5 input correspond to 5 output. Then, there are three independant wirings. It the same principle with Half-rotor (they emulates the Vigenere cipher): there are 10 starting positions but only 2 wirings. A position on two corresponds to a different wiring.

|

|

|
| Outside left | Outside right (the crank) | Inside right (the tape) |

|
|
|
| The lid | Inside left | Outside front |
|
|
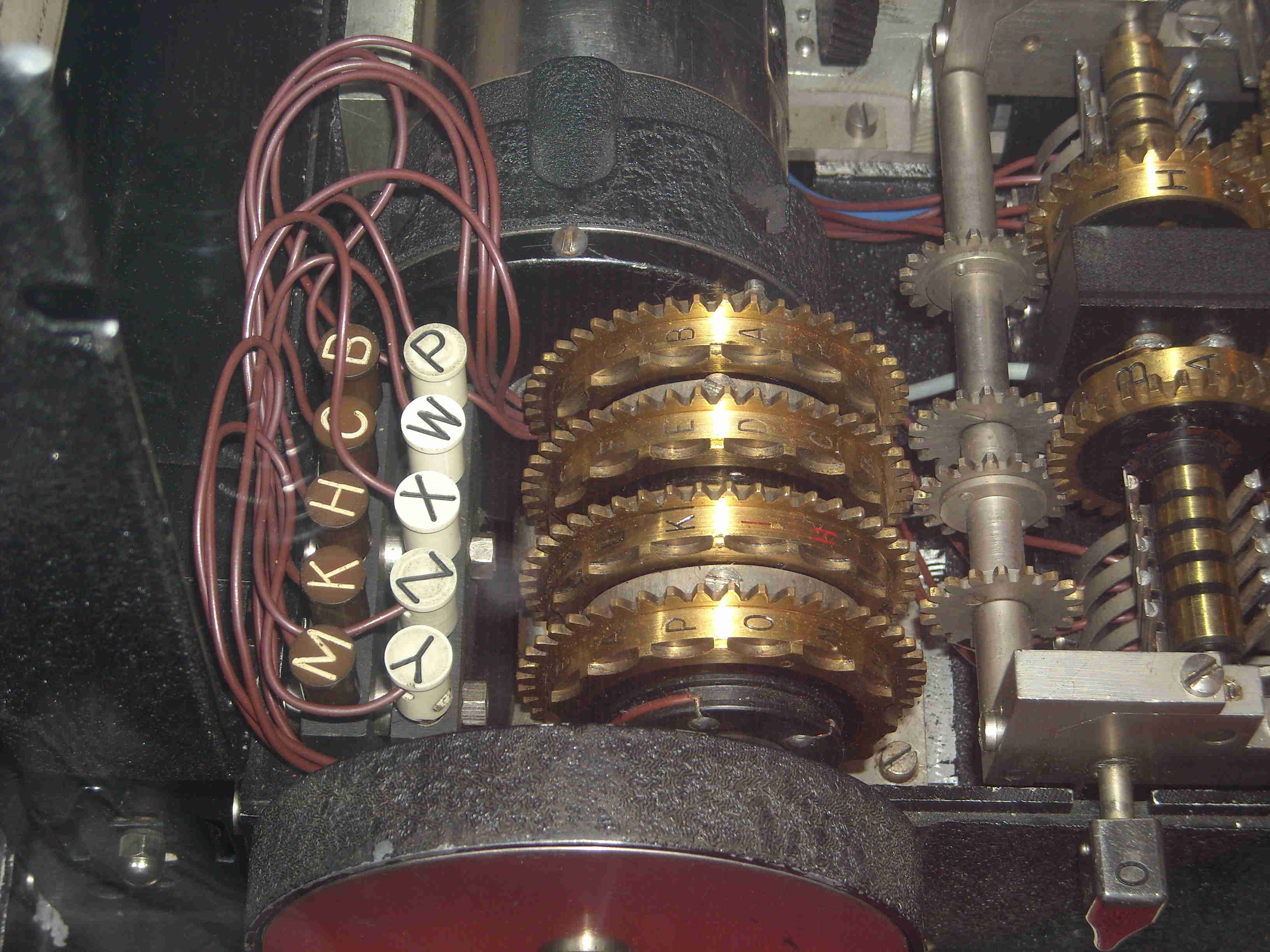
|
| Rotors and Half-rotors | Print mechanism | Super encipherment device |
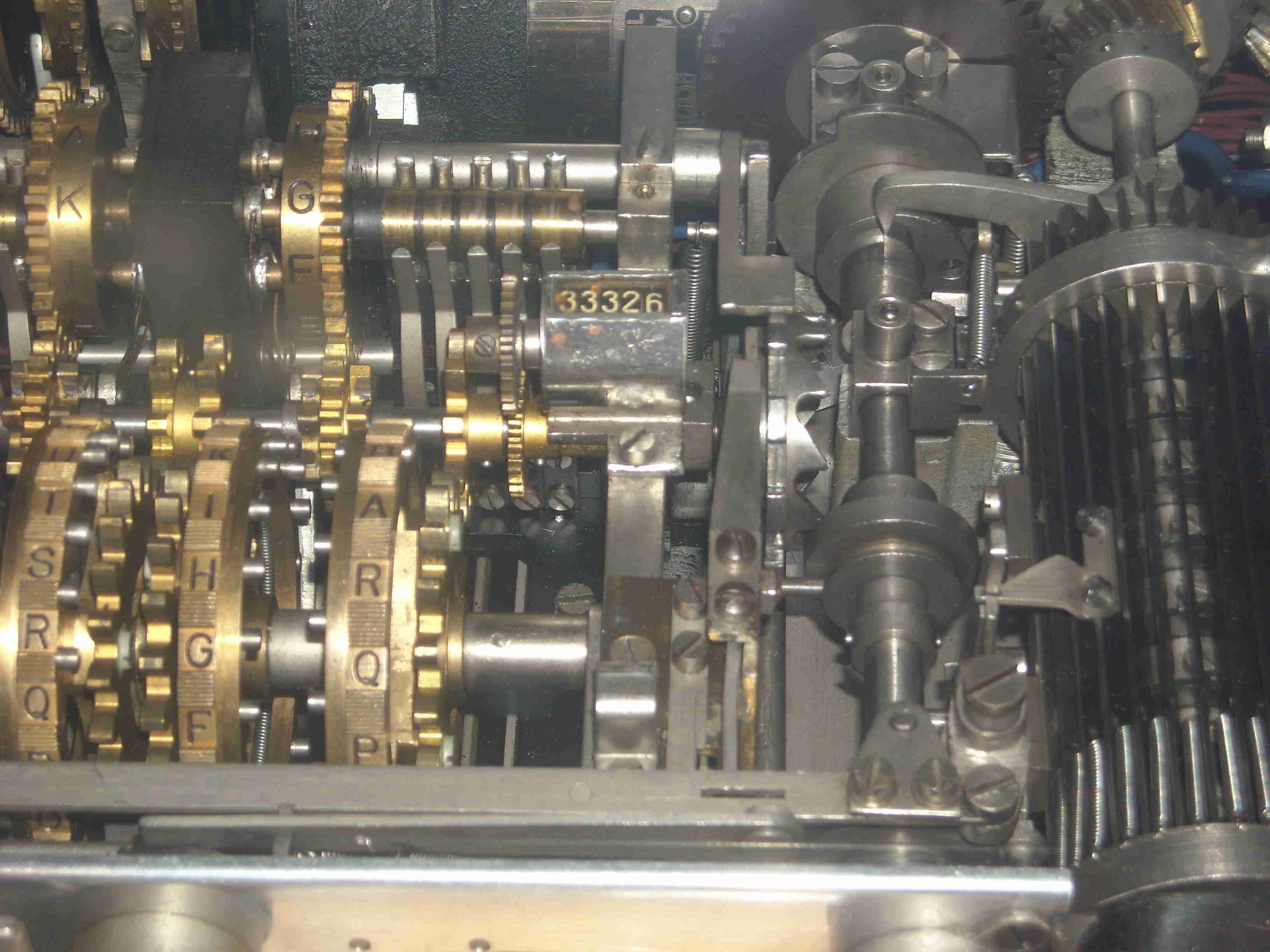
|

|
|
| Pins Wheels | The lid |
An example of encryption (with B-21)
Basic Key
Keyboard Grid (5x5):
L N R S T (consonant)
(v) 0 1 2 3 4
A 0 L M Y F X
E 1 O J B R S
I 2 P U G C W
O 3 K N T D Q
U 4 I H V E A
Plugboards: AEIOU and LNRST
Half-rotors:
Vowel Rotor: Consonnant Rotor:
A 01243 A 23104
B 32410 B 34201
C 12304 C 12043
D 43021 D 23140
E 23410 E 01432
F 04132 F 12034
G 34021 G 40321
H 10243 H 01423
I 40132 I 34210
K 21304 K 40312
Internal Key
Plugboards: OIAUE:LRNTS (32041:02143) Wheel 23: _B_D_F_H_K___OP___T_V__ Wheel 21: A_C_E__HIK_M___QR__U_ Wheel 19: _B_D___H_K_MN__Q__T Wheel 17: _BC__F__I_L_N_P__ WARNING! When apparent setting is AAAA, the effective setting of Pins Wheels will be GFHG. Note: The wheels and half-rotors advance before encryption operation.External Key: AAAAAA (active pins are: GFHG)
Plain text : HASTE MAKES WASTE Cipher test: QBVPD TUBAD VAPUT 1 2 3 4 5 6 7 8 9 0 1 2 3 14 H :H 1 G 0 I 0 H 0 : B A ! U N - A S - O T : Q A :I 0 H 1 K 1 I 1 : C B ! U T - U N - E R : B S :K 1 I 1 L 0 K 0 : D B ! E T - O N - U R : V T :L 0 K 1 M 1 L 1 : E C ! O R - E L - I L : P E :M 0 L 0 N 1 M 0 : E D ! U S - A T - O S : D M :N 0 M 1 O 0 N 1 : F E ! A N - A N - O R : T A :O 1 N 0 P 0 O 0 : G E ! U T - E R - I N : U K :P 1 O 0 Q 1 P 1 : H F ! O L - U N - E R : B E :Q 0 P 0 R 0 Q 0 : H F ! U S - O S - U T : A S :R 0 Q 1 S 0 R 0 : I F ! E T - A T - O S : D W :S 0 R 1 T 1 A 0 : K G ! I T - O N - U R : V A :T 1 S 0 A 0 B 1 : A H ! U T - O S - U T : A S :U 0 T 0 B 1 C 1 : A I ! E T - E L - I L : P T :V 1 U 1 C 0 D 0 : B I ! O R - E R - I N : U E :X 0 V 0 D 1 E 0 : B K ! U S - A N - O R : T Note: External Key after encryption: BK QQQQ (active pins: XVDE)Column Meaning
1 The input letter (plain letter or ciphered letter)
2 The current Pin of the Wheel 23 [1 = active, 0=inactive]
3 The current Pin of the Wheel 21
4 The current Pin of the Wheel 19
5 The current Pin of the Wheel 17
6 Vowel table position (of the first half-rotor)
7 Consonant table position (of the second half-rotor)
8 Vowel component of fractionalization (on ciphering mode)
9 Consonant component of fractionalization
10 Vowel substitution by the first half-rotor (on ciphering mode)
11 Consonent component by the second half-rotor
12 Vowel component after the plugboard (on ciphering mode)
13 Consonent component after the plugboard
14 The output letter (ciphered letter or plain letter)
Cryptanalysis
Before World War II
In 1931, W. F. Friedman asked to his students, Solomon Kullback, Frank Rowlett, Abraham Sinkov and John Hurt, to design a method to break the B-211 cipher. They managed to do that and published the following document: "Analysis of the Hagelin Cryptograph Type B-211". In 2016, it is still classified by NSA.In 1954, FBI arrested J.S. Petersen, an NSA employee. Over a decade he supplied Dutch with a stream of ducuments, among them the 1939 version of the Analysis of B-211. Dutch used B-211 (M1) for high-level diplomatic communications.
World War II
During World War II, German succed to break B-211 code ... but only the M1 model.Free French Forces supplied the US a copy of the M2 but with a different wiring from the actual one. The US approved the machine for high-level French exchanges. US cryptographic services could not break this code.
After the World War II
After the WWII, Americans succeeded to break the M2 code. They used at first cryptanalytic machines, then computers.Until the 1940s, cryptanalysis was entirely done manually. After WWII and until 1955, Americans have developed specialized cryptanalytic machines known as RAM (Rapid Analytic Machinery). Several of these specialized machines were developed against Hagelin B-211 cipher machines.
From the years 1955 computer use is spreading as the ultimate weapon for breaking codes (Harvest system for example). The old RAM were replaced by simple computer programs.
B-211 SteckerFinder
This machine, designed in 1947 by ASA, used a statistic analysis to find steckers (Plugs setting). This machine is still classified.FROG
FROG (B-211 Cribdragger) is an electric message setter for solving traffic from a straight-plugged B-211 cipher machine. It was designed in 1950. A maximum crib of 20 letters is used. A crib can be tested in all positions of 500 letter message in about 6 or 7 hours.Geewhizzer I-IV
This machine was used for several targets, one of them is the B-211 when the indicator is known.B-211 Analog
This machine simulates completly the working of the B-211 cipher machine. It was build in 1944 and was still operational in 1954.B-211 Handtester
This machine simulates the actions of commutators (plugs) and rotors of the B-211. A clerk uses it to find the Wheels setting. All wheels are moved by hand.Public methods
No method of attack of the B-211 was openly published. The only document on B-211 cryptanalysis is found in the book of Cipher A. Deavours and Louis Kruh (Machine Cryptography and modern cryptanlysis). It explains how to find the External key with a crib.Simulators
I have written two graphical simulators, the first emulates the B-21, the second emulates the B-211. I used the Python language version 2.x. The Python interpreter must be installed if you want to play my simulators.
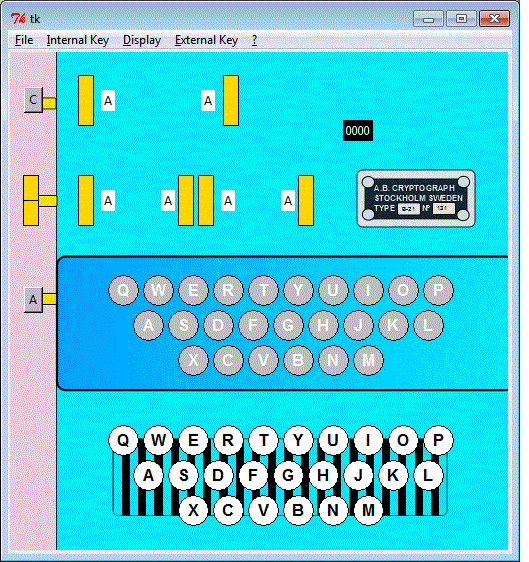
|
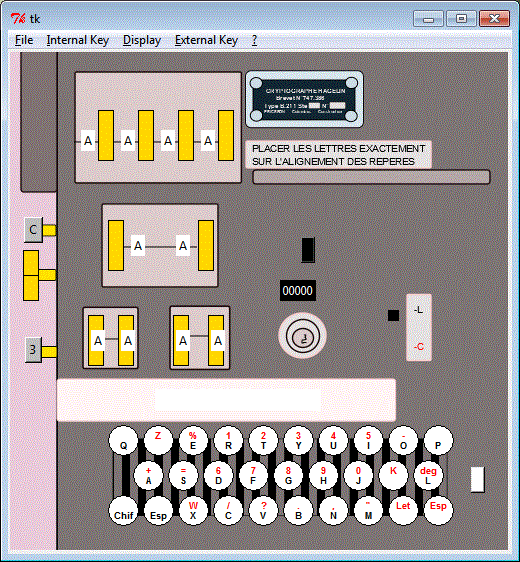
|
References
- [1]. Les écritures secrètes, by Adnré Muller, Presses Universitaires de France, 1971. In the chapter about cipher machines, the French B-211 (M1) is discribed in detail (including the keyboard splitting table).
- [2]. Machine Cryptography and Modern Cryptanalysis, by Cipher A. Deavours and Louis Kruh, 1985. This book (and the following reference) contains an example of encryption. Splitting of each character of the keyboard, the action of the half-rotors and plugboard action is described for each enciphered letter.
- [3]. Military Cryptanlytics Part II – Volume 2, by Lambros D. Callimahos and William F. Friedman, From Aegean Park Press.
- [4]. Instruction sur le fonctionnement et l'entretien de la Machine à Chiffrer Hagelin Type B-211, N° 125 CH./CAB, 29 Mars 1943. This document was classified "Secret". Unhappily this document doesn't explain the super-encipherment device. Only the M1 model is discribed. This document is written in French. I have written an exercpt in English.
- [5]. CryptoMuseum - Hagelin B-21
- [6]. Crypto-Museum. Hagelin B-211. You can see pictures of the M1 model. You can read the story of Soviet B-211 machine too.
- [7]. TICOM I-58, Interview of Dr. Otto Buggisch. In 1942, He solved back traffic (two years), but he was unable to solve actual traffic. The B-211 was changed (M1 was replaced by M2).
- [8]. Christos Triantafyllopoulos - French Hagelin cipher machines, B-211. The German called B-211 "F-20". American and German were able to read M1 traffic but weren't able to read the traffic from the modified machine (M2).
- [9]. The Hagelin, B-21 and B-211 John J. G. Savard,
- [10]. D'Hagelin à Rita, ARCSI, B-211. You can see a picture of a M1 model : the motor and battery is present. On the CGHQ pictures, these elements are missing. A slide gives a description of the super-encipherment device. I'm not sure this description is completly accurate (I think the plugboards are not correctly placed).
- [11]. Crypto Machine, Jerry Proc, B-21
- [12]. The Story of the Hagelin cryptos, by Boris C. W. Hagelin, Edited by David Kahn, Cryptologia, July 1994. The memoires of B. Hagelin can also be found on line on the Crypto-museum site.
- [13]. L'histoire de la machine Myosotis, Xavier Ameil, Jean-Pierre Vasseur et Gilles Ruggiu.
- [14]. NSA - Cryptanalytic Machines in NSA - 1953.
- [15]. NSA - Mechanization in support of COMINT Phase II- This document classified 'TOP SECRET' (declassified in 2013) describes in detail the B-211 model 2.
- [16]. Dirk Rijmenants - Hagelin B-21 Cipher Machine - ( B-21), You can see the US patent draw.
- [17]. Christos Triantafyllopoulos - The soviet K-37 Cristal cipher machine.