M-209: German break
-
German reconstruction of the internal setting:
German method
Morris's attack -
Get Plain text from messages in depth:
General method
German strip method
TM 11-380 (1947) -
Probable word attack:
Italian method
German method - Is a depth?
- Absolute setting
- Paper analog
Introduction
As soon as the M-209 was introduced in the war theater (in North Africa), it was broken by German cryptanalysts, especially from the OKH/Chi agency.The breaking of a daily key was a huge job. All operations were done manually. It took about a week to find a key and often much more. The German cryptanalysts only solved by depths the M-209 traffic. But they solved a large number of messages (perhaps about 10%) [TICOM IF-107].
German cryptanalysts named the M-209 AM-1 (Amerikanische Maschine 1=American cipher Machine one) and Sigaba, AM-2 (American cipher Machine two).
In the U.S. Army, the M-209 was used as a tactical cipher means in military units division level and below. Conversely, the Sigaba was used at the top levels military hierarchy from Army Corps level. Excerpts of TICOM DF-120: "Sometimes, however, even the corps use it (M-209)."
First Break
Excerpts of TICOM DF-120:The first use of the machine by the Americans occured in December 1942 in the African theater of war. The messages are recognizable through two 5-letter indicator groups at the beginning of the message of the type AABCD EFGXY, which are repeated at the end of the message.
The first messages in depth, that is, messages with like indicator groups, appeared in January 1943. Since it was a matter of exceptionally long messages of 682 letters, the entry into the entire system succeeded with them. The two messages were linguistically solved and the first internal machine setting found analytically.
When in April and May 1943, the then widely used strip system, known as M-94, was supplanted by this machine, we could read this new traffic currently as long as messages in depth apparead.
Remark (from other TICOM documents [IF-107 and I-211]):
Without ever having seen the m-209, Dr. Luzius and his colleagues
(Dr. Rinow and Steinberg) of OKH/Chi determined the design of the
machine from two messages "in depth" of 700 characters in January
1943. By the way they determined the actual setting.
Messages in depth
Definition
Two different messages are in depth when they are ciphered by one signal net, on the same day, and with and indentical starting position of all wheels - same external indicator - so that internal and external setting are identical.Importance of Depth
The German cryptanalysts only solved by depths the M-209 traffic. Why were so many depths?How occur depths
This may be subsequent messages of one station, or a message and the answer thereon, the operator of the 2nd message or the answer turning back the converter to the starting position of the 1st message and neglecting to change the external setting, for the 2nd message or the answer.Cillies
Excerpt of Signal Corps Technical Information Letter - Dec 1944Unless closely supervised, code clerks tend to make two types of mistakes with indicators. They choose words like BERLIN, MAISIE or GTHREE for their indicators {but also SESAME, BUSTER, ZOMBIE, ADOLPH, HEPCAT...}. They use some mechanical method of selecting indicators which produces nonrandom groups.
Use of the same indicator more than once for M-209 messages permits those message to be broken easily, and subjects the entire system to compromise. If indicators are not chosen at random, repetitions are inevitable. The man who chooses MAISIE supposes that he is alone in his choice. Actually there may be several code clerks who are also partial to Maisie and equally inclined to choose her name.
The usual decryption procedure
In the following paragraphs, we will describe in details the various stages of the decryption process.1. Interception
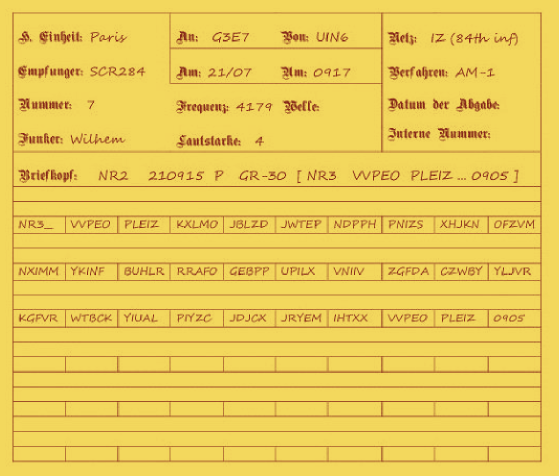
Before finding keys and deciphering M-209 messages, Germans needed to intercept these messages. The different German Sigint agencies (of OKH or OKL, ...) had intercept stations where soldiers listen to enemy radio messages. They filed forms which stored all about the messages and the intercept conditions.Here are the different fields of the form:
- Intercept Station (“H. Einheit”)
- Receiver (“Empfünger”)
- Serial Number (“Nummer”)
- Name of the operator (“Funker”)
- Frequency/Waves (“Frequenz”/”Welle”)
- Signal Strength (“Lautstärke”)
- Remarks (example: jamming)
- Sending station (call sign with meaning if possible) (“Von”)
- Addressee (call sign with meaning if possible) (“An”)
- Day date (“Am”)
- Precise clock time (hour and minutes) (“Um”)
- Headings (“Briefkopf”): message number, tactical time, groups count, indicator groups, ...
- Network (“Netz”): the net can be filled in by traffic analyst.
- Method (“Verfahren”): it is the cryptographic system used. This entry is filled by traffic analyst.
- The time when the deciphered message is (“Datum der Abgabe”)
- The number from the Worker in the cryptanalytic section (“Interne Nummer”)
- The cryptogram
- The plain message (if it was deciphered)
2. Sorting, extracting of messages in depth
At first, the messages are sorted according to their cryptographic system. All M-209 messages can be easily recognized because the two first letters of the indicator are the same. The two indicators groups are placed in the beginning and ending of the message.Then, the messages are sorted according to their cryptographic network (all stations which share the same key-list). The two last letters of the indicator precisely indicate this network. The code clerk who created the cryptogram can hide the network by repeating the two first letters of the indicator. Then to find the network the traffic analyst needs to base his deduction only on call signs.
The final step is to sort messages according to indicators. When the traffic analyst finds two messages with the same indicator, he can suppose that the messages are in depth.
Remarks:
the lists of intercepts with indicators were exchanged between intercepts
stations from the Army (“Heer”) and Air Force (“Luftwaffe”).
At the end of DF-120 you can see lists of indicators.
3. Verifying depth
Recovering plain text from messages in depth is very time consumming. Before undertaking this task we must be sure that the messages are in depth.Indeed, when the same message is repeated because there are errors inside, it is frequent that only a part of the message is in depth.
In TICOM DF-120 document, German cryptanalysts describe several methods which can help to decide whether two messages (or part of) are in depth or not.
Remark: I have described the German methods in another document.
4. Finding plain text
Suppose there are two messages encrypted with the same key. Next, search for probable words in one of the two texts. Eg ZPARENZ chain was very common (it framed addresses). The probable word is placed at each position of the first text and we try to decipher the text of the 2nd message at the same position. If at a given position, plain text appears, it was proved that the probable word was actually used. Also known its position in the first text, we also find another probable word in the second text. Then we try to guess the text before and after each probable word. After many trials / errors, we can determine the entire plain text of the two Cryptograms.By using strips of paper, the Germans accelerated the finding of plain text. The cryptanalyst Alfred Pokorn created a stuff to print the strips.
Remarks:
- I have written an example of finding the plain text from messages in depth.
- I have written a computer program which can generate strips from messages in depth.
- I have written another computer program which can search for plain text from messages in depth but without using strips.
- The M-209 Manual TM 11-380 (1947) describes how to get plain text from a depth.
5. Finding the Internal relative setting
The technique of resolving key was the obvious one of writing out the key on all wheel periods and looking for the high kick wheels first.It is necessary to have a minimum 60 elements of key for reconstruction of pin and lug settings. It is possible with about 40 elements but it is very difficult.
The reconstruction of internal settings is much more difficult when the number of overlaps is heavy.
Remarks:
- I have written an example of using of Morris's method (largely similar to the German method).
- I described German method too.
6. Sovling others (or another) message(s) by probable word method
Each message in a period of time (a day for example) are encrypted with the same basic key (Pins and Wheels setting). But each message is encrypted with a different message key (the initial position of the wheels).Before the Internal absolute setting recovery method was devised, the German cryptanalysts had to get the external key for each message. The probable word method was used. Here too, the word ZPARENZ was very frequently tested.
After the development of the Absolute setting recovery method, the deciphering of a third message by probable word method allowed to accelarate the process.
Remarks:
- I have written an example of finding the relative external key by probable word method.
- I have described too the german method, but with the same example used in the above document.
7. Finding the Absolute setting
It is possible to find the Absolute pin and lug settings from only one indicator, but the process is very long. The cryptanalysts need to try every start wheel setting. This method is described in the TICOM I-175. I wrote an excerpt of this document with a personal example.Another method, described in TICOM DF-105 document, based on the earlier one, is to use a second indicator. But the cryptanalyst needs to decipher before another message. He uses the probable word method described in the last section.
I wrote a program that finds the absolute setting (absolu3.py). Its algorithm is very simple: one explores all the possible keys, and for each one we encrypt 12 times the doubled letter. Then we can deduce the message key which is then tested (program)
8. Decrypting all messages of the Day
As soon as the German cryptanalysts get the Absolute Lug and Pin settings, they are able to solve all messages of the same network, i.e. ciphered with the same key-list (usually valid only one day) as a normal U.S. code clerk.Most of German cryptanalysts lacked a M-209. Instead they used a Paper analog.
As soon as a team recovered a key it informed the other by radio. Unfortunately for the Germans, in 1944, Bletchley Park read these encrypted messages ciphered by means of Enigma (Pigeon Key).
9. Translation and Evaluation
After dechiffering, the messages were translated in German and finally Evaluated in order to draw intelligence by SIGINT regiments (KONA). Then the informations was transmitted to their assigned Army Corps HQ.Because of the slow deciphering (several days, even one or two weeks), little tactical intelligence was deduced, but an appreciable amount of strategic intelligence was obtained (Allied order of battle, the bulding of new airfields, effect of German V1 bombs, ...).
Other methods
We have described the main line decryption based on two messages in depth. The German cryptanalysts exploited other encryption errors:- Two messages with the same indicator except the two first letters.
- Two messages with the same indicator but with one wheel with different start setting.
- The same plain text in a second message in depth with the first but in a position differing by one or more letters (Stagger phenomena).
1. Two messages with the same indicator except the two first letters
When there are two identical messages available, ciphered by one signal net, on the same day, and with an identical initial position of the wheels, but with a starting position deplaced by one or two letters (or pins) equally on all wheels.This results by printing another single letter, than the two first letters of the external indicator, for changing the initial wheel position to the starting position, in the 1st message. The 2nd message is correct repetition of the 1st, with identical external indicator. If the correct single letter differs from that used for ciphering message I, by one letter of the alphabet (e.g. M and N), the starting position of both messages will also differ by one letter - or pin position on all wheels. Same for two (and more) letters, so long as no letters are printed, that could not be turned on on the respective wheel.
Remark: it is a special form of 'messages in depth'
2. Two messages with the same indicator ... with different start setting
When there are two indentical messages available, ciphered by one signal net, on the same day, and with an identical starting position of 4 or 5 wheels only, but with the same external indicator, so that internal settings are identical and external settings differ slightly.This results by an error in the setting of the wheels to starting position, the typing of the single letter e.g. RSQRFJ and the operator turning the wheels to RSORFJ, in the 1st message. The 2nd message is a correct repetition of the 1st, with identical external indicator.
Remarks:
- I haven't found any details of this method in TICOM documents.
- I haven't been able to solve messages when this special case appears.
3. The same clear text ...(Stagger phenomena)
When a cryptographer makes the mistake of enciphering the same message twice, and makes the error along the text (into one message), to add or to forget one or two letters. This situation is named 'stagger.'Remark: Stagger is a special form of 'messages in depth'
Captures
During the war, several M-209, manuals and even key-lists were captured.We know at least these appearances:
- Key-list of a month was captured at the end of the African campain (perhaps May 1943) [TICOM I-95].
- Key-list of June 1943 was captured in Sicily. The capture was not reported and the traffic was read during the entire month [TICOM IF-107].
- Key-list of July 1943 was captured in Sicily. This pinch was towards the end of the month in consequence the Germans read traffic only for a few days [TICOM I-93].
- In the Nettuno bridgehead (Anzio area), the keys-list of January 1944 of the 45th U.S. Division was captured [TICOM I-23].
- Key-list from 6 to 11 June 1944 (D-day, D-day+1, D-day+2, ... D-day+5) were captured in Normandy.
- Key-list of October, 1944.
American countermeasures
At the end of the war, the Germans took many countermeasures to improve the security of Enigma: The appearance of new keys (new networks), Abandonment of Kengruppe (Network indicator), using of Wahlworts (nonsense word) and CY procedure (changing a wheel setting in middle of a message). The Enigma itself was modified (using of the D Reflector).Similarly, the security of the M-209 was improved:
- A greater number of keys (see below)
- Bisection
- Padding
- Paraphrasing
- A huge number of abbreviations
- The numbers
are not spelled out anymore but are sent as double letters:
1 is aa, 2 is bb, 3 is cc, … 0 is jj. - The decreasing use of the word PAREN (see below)
- The establishment of a monitoring system (see below)
A greater number of keys
Excerpt of "European Axis Signal Intelligence in World War II, vol 5":The analysis of the M-209 was made more difficult when each army and command began using separate settings.
At the end of war, the German cryptanalysts were facing a very large number of keys, sometimes, as many as 75 different keys were being used simultaneously, each division and corps being provided with its own set of keys, as were the numerous Military Police battalions and units of the Army Air Forces.
The large number of keys helped to the deciphering of Enigma messages, because of large number of recryptographed messages. In case of M-209, no TICOM document indicates that these recryptographed messages have been used regularly. Maybe the rules of paraphrasing [TM 11-469] were better applied by American code clerks.
A monitoring system
The Americans put up a real system of supervision of the use of their encryption systems.
Excerpt of "The Achievments of the Signal Security Agency (SSA) in
World War II, 1946."
A security study of ETO (European Theater of Operations)
traffic in the spring of 1944 let to the
recovery of keys for a number of days and decipherment of all
traffic for those days by SSA cryptanalysts.
The decreasing use of the word PAREN
The word PAREN (or "ZPARENZ") was the most frequent probable word in American messages because it framed addresses.At the end of war, Americans began to use several alternatives to this word: CMA, PD, CLN, XXX.
In addition, the use of addresses in the text was not recommended. Conversely, the exclusive use of callsigns for specifying addresses was strongly recommended.
Organisation
The principal agency which broke M-209 messages was the German Army (OKH/Chi). The German Air Force (Chi Stelle) broke some messages too. The Army and Air Force exchanged informations (interceptions, methods, keys, ...).The mission of the Army Signal Intelligence Service (known as Inspectorate 7/VI, thereafter known as OKH/GdNA, the Oberkommando ders Heeres/General der Nachrichten Autklaerung) was the interception and cryptanalysis of foreign military communications.
The German Army’s field signal intelligence effort was organized into nine SIGINT regiments (known as KONAs, Kommandeur der Nachrichten Aufklaerung) stationed on every front. They were organized as complete interception and evaluation units providing a full set of services including interception, traffic analysis, direction finding and evaluation and translation services to provide tactical intelligence to their assigned Army groups.
The M-209 cryptanalysis was based on the division of labor: one team finds the plain text from a depth and deduces the internal settings. Another team finds the Absolute setting. Then, a final team deciphers messages.
All work was done by hand. Sometimes the indicators sorting was done using Hollerith systems.
It took about two days to solve a depth and reconstruct the internal settings. Then it usually took two more days to derive the absolute settings. As a result of this and delays in obtaining intercepts it was usally at least a week before a day's traffic was fully out.
The cryptanalysts were located at two different places: At Berlin and at the HeadQuarters of the Army front of the enemy. Copies of all intercepts were sent to Berlin and apparently the cryptanalysts at Berlin HeadQuarters competed with those in the field in an effort to obtain solutions as rapidly as possible.
For example, W.K.G. Graupe's unit received 200-250 messages by day. The percentage of keys read was about 10%.
Examples of clear text
In TICOM I-175 document, Alfred Pokorn remembered several samples of clear text which was intercepted and deciphered:- Supplies:
- Laundry open at once near cross-road 832045. Secure large envelope from under Novaks jeep seat. Send ten tonner for ammo. to ....
- Tactical:
- C.P. at 830716. Headache red advancing N.E., no resistance. Rechicourt occupied at 1400 hours., 744018.
- Air Support:
- Bomb line bridge 273406, then railway to ... Your demand accepted. Aspo. GRAZ bombed by instruments.
- Personal:
- Send pass for Sgt. White to go to PARIS tomorrow. Lt. Black is to report to this HQ to be promoted. Report 2 o., 4nco. 290 em.
- Signalling:
- Traffic report, out 10 secret, 20 confidential, 150 ordinary messages, in 12 secret, 16 confidential, 125 ordinary messages,
In TICOM archives (DF-120) we can find two authentic messages encrypted with the machine M-209.
Mechanization
We have just stated that the Germans only use manual methods.Exceptionally, they used hollerith machines to sort indicators. These machines were also used to find messages in depth, but for other systems (codes), not for the M209.
Dr. Huettenhain of the Signal intelligence Agency of Supreme Command, Armed Forces (OKW/Chi) stated that M-209 depths were found by using "Fasensuchgeraet", a rapid analytic machine, probably the "digraphic weight recoder" described in TICOM I-31. Unfortunately, this document is obscured in part by a large white rectangle. in short, it is still classified.
After the war, Americans found the blue print (TICOM DF-114) of a weird machine (some people are nicknamed it "German Bombe"), which was to assist in deciphering the M209. Its use is not obvious. In my opinion, this stuff was used to find the absolute Pins and Lugs setting.
Comparison of Enigma and M-209 cryptanalysis
Enigma and M-209 are cipher machines very safe when properly used. Thus the Enigma army key Greenshank has almost never been broken.At Bletchley Park, The British Cryptanalysis of the Enigma was essentially based on three German clerk errors:
-
Cribs
A Crib is a short section of plaintext thought to be somewhere in the ciphertext. A crib is easy found in routine messages, for example: "KEINE BESONDEREN EREIGNISSE" (no special developments) -
Cillies
The use of easily guessed keys (such as AAA or BBB, ...), was called cillies. -
Re-encodements
Re-transmitting messages that had been sent either from a low-level cipher (Dockyard cipher for example), or from another Enigma network.
Conversely, the main error comised by US cipher clerk is reusing the same external key (messages in depth).
I haven't never seen mention of Cillies in TICOM documents. Perhaps the Americans prevents cipher clerks of this danger.
In TICOM documents, I saw only once the reference to the use of cribs to solve a key. But this method has been very useful for finding the keys of the French cipher machine Hagelin C-36 (very close to the M-209). Perhaps the use of bisection and padding by American clerks prevented the exploitation of cribs. It should also be noted that the lugs and overlaps impede Pins setting determination when a crib is used.
I haven't never seen mention of re-encodements usage in TICOM documents (neither from different M-209 networks nor a different system such as M-94). Perhaps the utilization of paraphrasing or variations of spacing by US clerks prevented the exploiting of this phenomena.
Remark: With Enigma, a letter could never be encrypted to itself (a consequence of the reflector). This feature helped British cryptanalysts to put in place a crib and to be sure of re-encodement presence.
Conclusion
In October 1950, a group of Britsh and American Cryptanalysts (among them W.F. Friedman and Abraham Sinkov) discussed about the M-209 security after the TICOM revelations.Here the main points:
- "Most of the sources stated that from 6 - 10% of the U.S. Army M-209 traffic was read."
-
"Mr. Friedman remarked that, since conditions were usually unfavorable,
a time lag of two or three weeks between interception and the obtaining
of the absolute settings for the M-209 traffic would not be improbable.
"Mr. Austin also cited the German Army cryptanalyst, Graupe, who gave an estimate of 5-7 days as the time necessary for obtaining the absolute setting.
-
" Mr. Perrin said that frontal solution of the M-209 was apparently
confined to the reading of messages in depth."
"Mr. Perring stated that the German cryptanalysts never developed a general method of solution, although there is a description of a theorical solution of the M-209, given a text of 3000-5000 letters."
- "...it is generally agreed that a considerable amount of American M-209 traffic was broken by the Germans during World War II, from which little tactical intelligence was deduced, but from which an appreciable amount of strategic intelligence was obtained."
M-209 Challenge
I created a challenge offering M-209 encrypted messages to decipher. Some of these problems are designed to be solved with German known (or assumed) methods .References
- Report by Alfred Pokorn of OKH/CHI, on M-209. TICOM I-175.
- "Report on the solution of messages in depth of the American cipher device M-209" TICOM DF-120.
- TICOM: Determination of the Absolute Setting of the AM-1 (M-209) by Using Two Messages with Different Indicators DF-105
- GERMAN CRYPTANALYTIC DEVICE FOR SOLUTION OF M-209 TRAFFIC - DF-114
- TICOM: Survey of Russian Military Systems DF-112 The standard Intercept Radio Form is described.
- TICOM Archive - Secret Intelligence in Nazi Germany GdNA
- Google - History of HUT 6 HW 43-70 vol1, p257
- NSA - Special conference on M-209 security
- NSA - European Axis Signal Intelligence in World War II, as revealed by "TICOM" investigations and by other prisoner of war interrogations and captured material, principaly German Volume 2 Volume 3 Volume 4 Volume 5
- The Achievments of the Signal Security Agency (SSA) in World War II, 1946.
- Signal Corps Technical Information Letter - December 1944
- Christos military and intelligence corner - The American M-209 cipher machine
-
Klaus Schmeh - Als deutscher Code-Knacker im Zweiten Weltkrieg -
( German code breakers during World War II)