M-209 - Making and managing Key-lists
TM 11-380,
Preparation of pin and lug settings:
Introduction
Deciding to use M-209 is one thing, set up an organization to use it securly is another.Each M-209 code clerk of the same network (the message centers of a Division for example) must share the same information which allow exchanging messages by means of this cipher machine: first, the rules for transmitting External key (thanks to the Indicator system); second, the cipher-key list. This one contains the Internal setting for the network. The internal key is composed by the pins and lugs setting.
However, several problems arise :
- How to specify to a recipient what key-list to be used? And even why using the M-209?
- What organizational unit must be responsable of all this stuff?
- How to distribute the key-list?
- How to secure the key-list?
- What should be the limits of use of a keylist? For example, how long can a key-list be valid?
- How can the code clerk verify the setting?
- Can a key-list be used for any message?
- What steps to take if a key-list is compromised?
- What should be the appearance of the key-list?
- And finally, How to create the Pins and Lugs setting, in another word, how to make key-lists?
How to specify to a recipient what key-list to be used?
The indicator is a string which is placed at the beginning and at the ending of a message. It indicates the crypto-system used, the key-net (then the key-list) and the External key. The rules to create or read an indicator are stored in the SOI.With the most used indicator system during WWII, the two first letters were the same. They indicated the use of M-209. The six following letters were used to derive the External-Key. The last two letters indicated the key-net. Each key-list was tagged with these two letters.
The code clerk can hide the network by repeating the two first letters of the indicator. Then to find the network the recipient needs to rely only on call signs.
What organizational unit was responsible?
The key-lists were prepared by the staff under control of the Signal Officer of the military unit. So, during WWII, each Division had a Signal Company directed by a Signal Officer. The staff was trained at Fort Monmouth.The key lists of a month were usually written in a document named SOI (Signal Operation Instructions).
How to manage the key-lists?
How to distribute the key-lists?
Each SOI (the document which contains Key-lists), contains a distribution list which indicates the different recipients and the number of copies they receive. Each SOI is numbered too.One can imagine that the distribution of keys was similar to an ordinary message. Each copy was physically conveyed by messenger. Each recipient must sign the distribution list; the message number being replaced by the copy number. A recipient can receive several copies.
How to secure the key-lists?
Excerpt of SOI 1943
- THE FOLLOWING SIGNAL OPERATION INSTRUCTIONS (SOI) ARE EFFECTIVE AS INDICATED ON THE INDIVIDUAL ITEMS. WHEN CHANGES ARE ISSUED THE ITEMS SUPERSEDED WILL BE DESTROYED BY BURNING.
- THE LOSS, CAPTURE OR COMPROMISE OF THIS SOI OR ANY PORTION THEREOF WILL BE REPORTED TO THIS HEAD- QUARTERS BY THE FASTEST MEANS AVAILABLE.
- THIS SOI NORMALLY WILL BE KEPT IN THE MSG CEN OF UNIT TO WHICH IT IS ISSUED. EXCEPT TO AVOID CAPTURE, IT WILL NOT BE REMOVED FROM CP OF THE UNIT
What steps to take if a keylist is compromised?
If a key-list was compromised (for example, if it was captured by enemy), the Signal Officer of the unit (for example the Division), warned each holder of SOI compromise and forbids its use. He immediately distributes the new version or requests the commissioning of an emergency key.Remarks:
- In TM 11-380 1947, the key-net indicator "EM" is reserved for Emergency keys.
- I have never seen any document mentioning a method for making special Emergency key. Conversely, the Germans used several methods to do this.
What should be the limits of use of a keylist?
There is a rule in cryptology: the more you create messages with the same key, greater the chance is that the enemy finds the key. In the particular case of the M-209, the more messages exist, the more superimpositions (messages in depth) occur.Then the usage of a key must be limited:
- The total number of groups for all messages must be limited. For example, in TM 11-380 1947, this rating is limited to 10,000 groups.
- The validity of a key must be limited in time. For example, during WWII, a key-list was valid only one day. The monthly SOI document contained the key-lists of a month, then about thirty key-lists.
How can the code clerk verify the setting?
Excerpt of the TM 11-380 1947Every pin and lug setting will be accompanied by a 26-letter check. Using this check, the operator of Converter M-209-(*) will verify his preliminary settings. The operator will always make the check after setting the pins and lugs, before any messages are enciphered or deciphered.
Remark : An error in setting may not appear in the 26-letter check.
Can a key-list be used for any message?
In a Division M-209 was used with the same key-list for RESTRICTED and CONFIDENTIAL messages. Simply, the word “RESTRICTED” was included in the message if this type of traffic was used.In an Army Corps, the Sigaba machine was to be used for all SECRET messages. In its absence the M-209 was used. In this case, the word “SECRET” was included in the message. On the other hand, in an Army Corps, different key-lists were provided for RESTRICTED and CONFIDENTIAL traffic.
Excerpt of TM 11-380 (M-209 Manual) – May 1947
c. Separate keys and separate key-list indicators
will be provided at all times for CONFIDENTIAL
and RESTRICTED traffic except within a division
(or smaller tactical unit) preparing its own pin
and lug settings. In such units, the same pin and
lug setting may be used for CONFIDENTIAL and
RESTRICTED traffic and the key-list indicators
omitted; all traffic will be considered CONFIDENTIAL
unless otherwise specified within the body
of the message. If a message is RESTRICTED, the
designation XX RESTRICTED XX will be buried
in the text before encrypting. When the key-list
indicator is omitted, the system indicator will be
substituted in its place, and will thus appear twice
in the two five-letter indicator groups.
...
i. Converter M-209-(*) will never be used for SECRET traffic except when a system normally authorized for SECRET traffic is not available. When a SECRET message must be enciphered by means of Converter M-209-(*), the CONFIDENTIAL key will be used and the word SECRET, set off by two X’s on each side, will be buried in the text before encrypting.
What should be the appearance of the key-list?
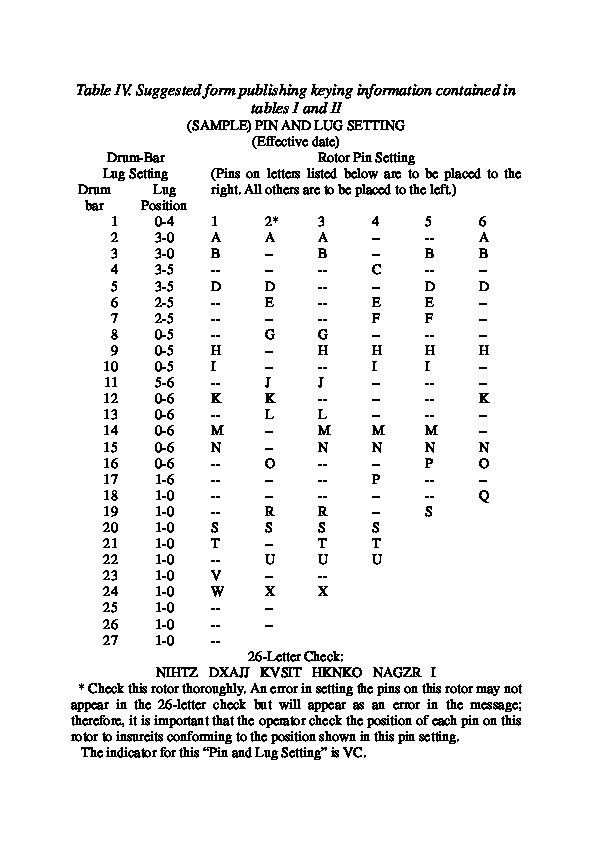
A M-209 key-list contains principally the lug settings and the Pin settings. But also the valid dates and the key-list indicator. Finally the 26-letter check is also present. Normally, the key-lists of the month, the indicator rules, the distribution list and call-signs are all included in the SOI of the military unit (Division, …) to which the message centers belong.The two configurations considered as a whole or not
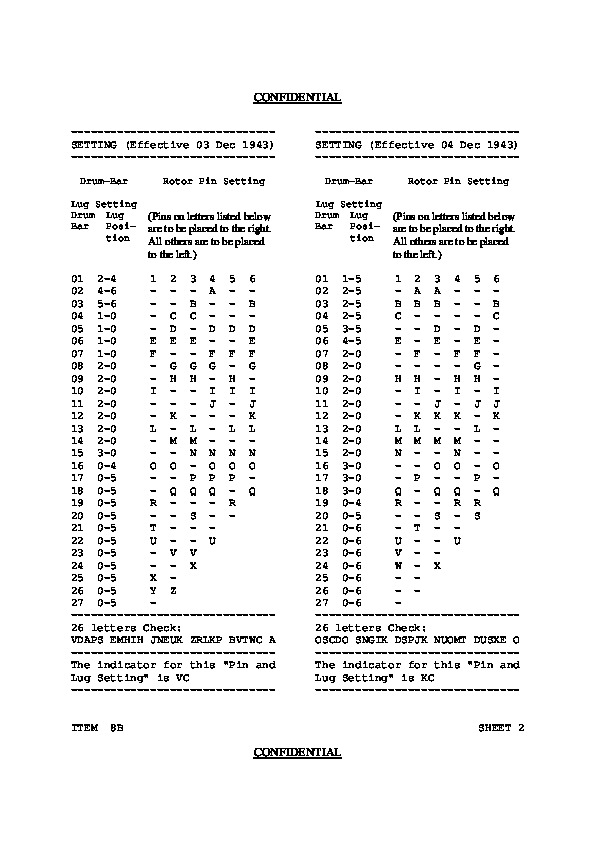
Making a key is a long process. If the life of the lug setting and that of the Pin setting are different (e.g. the configuration of the valid Pins one month and that of the lugs fifteen days), this reduces the total number of settings to be created for the same number of internal setting.One can also form the key to a period as the combination of several key configurations. For example the first day, one uses the configuration Pins # 3 and the configuration Lugs # 6, the 2nd day, the configuration of Pins #1 and the configuration Lugs # 3, the 3rd day, the configuration Pins # 3 and configuring Lugs # 3, etc. The latter strategy is that used in the 1943 SOI. Again it reduces the number of keys to create.
Security: The keys-tables in naval Enigma used a configuration of daily
plugs but the same wheels configuration two days in a row. This allowed
the Allies to find many keys. It is for this reason that in the manual
TM 11-380 1947, a M-209 Internal-key is a whole that every time takes
a new configuration of Pins and Lugs. In addition, it is explicitly
forbidden to reuse part of the configuration (Pins Lugs) to create a
new key:
Excerpt of TM 11-380 1947:
"Never use a previously used pin setting in combination with a different
lug setting, and never use a previously used lug setting in combination
withe a different pin setting".
If the lug setting and pin setting are synchrone, normally these settings are on the same sheet of paper, but they can be on different sheets.
Representation of Pin settings
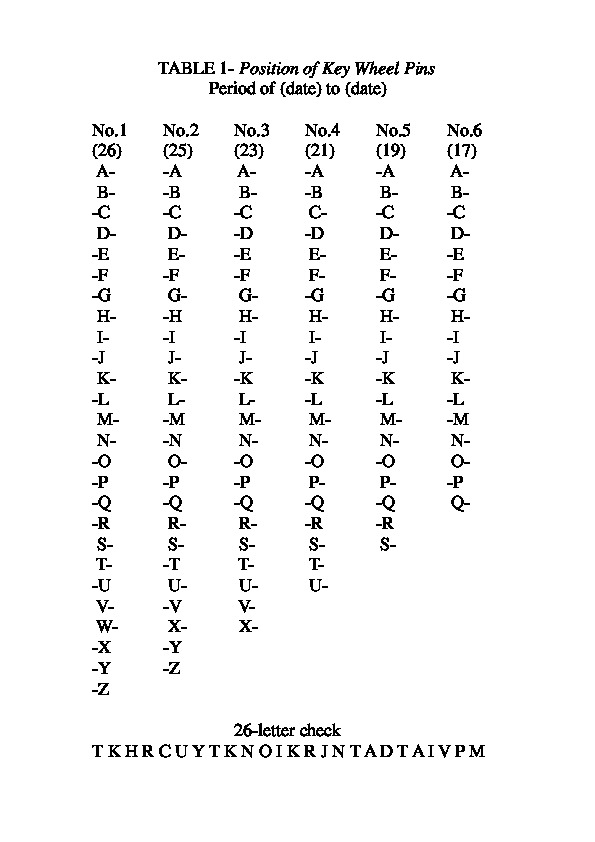
There are several types of representation of Pin setting:- At first, in 1942, Each Pin of each wheel is designated by its letter with the minus sign on the left or on the right to indicate if the Pin is effective or not. For example, "-A" indicates that the pin designated by the letter A is to be placed in the left position and "A-" indicates that the pin of letter A on the key wheel in question is to be pushed to the right,
- Since 1944, Each letter with a Pin active is printed, but the letter is replaced by a underline sign if the Pin of the correspondent letter is inactive. For example "A _ _ D E _" means that Pins designated by letters A, D and E are active and Pins B, C and F are inactive.
Representation of Lug settings
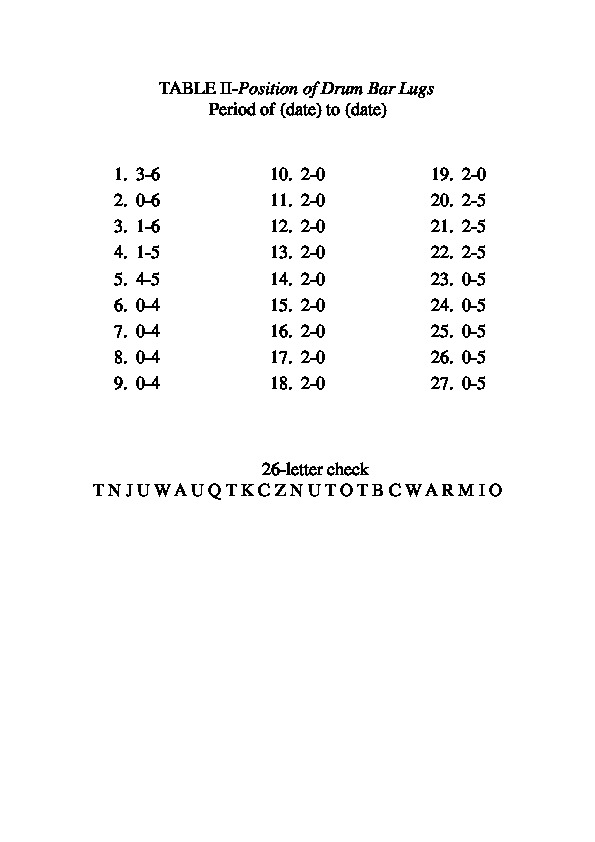
In this case also, there are multiple representations of the configuration :- At first, in 1942, the Lugs setting was represented by an array where each row represents a bar. An effective Lug in front of a wheel is represented by a cross in the column associated with a wheel.
- Since 1944, the two lugs of a bar are represented by a couple of numbers. If a lug is active, its value represents the wheel in front of it is. If the lug is inactive, its value is zero.
Key-list in recent SOI
There is a Video which explains how to use the M-209. We can see key-lists from a SOI. There are two key-lists in the same page. Furthermore, the Lugs and Pins configuration is together like the TM 11-380 1947.Remark: We only talked about US key-list. Maybe other countries using a C-38 had a different representation of a key-list. I imagined, as an example an Italian key-list.
|

|
|
| TM 11-380, 1942: Pins | TM 11-380, 1942: Lugs | TM 11-380, 1947: Pins & Lugs |

|
|
|
| TM 11-380, 1944: Pins | TM 11-380, 1944: Lugs | SOI 1947: Reconstitution |

|

|

|
| SOI 1943: 26-letter check | SOI 1943: Pin Settings | SOI 1943: Lug Settings |
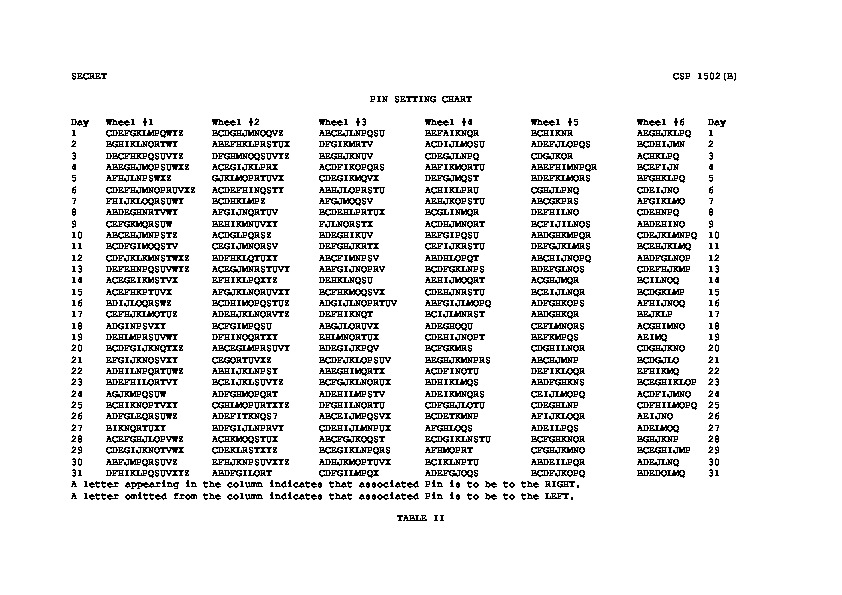
|

|
| Navy 1942: Pin Settings | Navy 1942: Lug Settings |
How to create the Pins and Lugs setting?
A good key
To make a good Pins configuration, it is easy : you choose at random each Pin value (effective or ineffective). It is wise to have an equal percentage of effective and ineffective Pins.To make a good Lugs configuration, it is not so easy. If we choose only by random a cage (setting of lugs of each bar), the result can be disastrous: for example [0,0,0,9,9,9]. The wheels 26, 25 and 23 have no effect on encryption and displacement values are only 0,1,9,18. It is very easy to decipher a crytogram from only the cipher-text with this key (cf. The book). A good cage is one that generates all possible keys in the range from 0 to 25.
From TICOM documents, it is clear that the number of overlaps is an important factor of security. Consequently, the 1947 rules require at least two overlaps (during the WWII, only one was required).
The preparation of the internal setting follows strict rules. Normally, it is only the Signal Officer who creates the key-lists, but the rules for their preparation are contained in each M-209 manual (TM 11-380). A small code clerck group can create their own key-list and their own indicator system. Depending on the version of the manual, the rules have evolved.
TM 11-380, Preparation of pin and lug settings
Several 1953 documents
Several documents dated 1953, indicates the rules used to create the array keys (Lugs and Pins setting). It is also indicated that these settings were created automatically by IBM hardware.Softwares which generate key-list
Mark Blair has published on his website a M-209 simulator. His program comes with a module that generates keylists.I also created a program that emulates the M-209 and generates keylists respecting the rules specified in the manual TM 11-380, versions 1942, 1944 and 1947.
Make a key manually
I created a key manually by following the procedure of the 1944 manual. It's very long to do it.The manual requests to create two sets of 78 cards with L (left) or R (right) on each card. In fact I used three sets of card game where a red card (heart or diamond) means R (right) and a black card (spade or club) means L (left).
After choosing a set in Group A or Group B, I have used a card game too. For each number, I take a card with the same value: an ace for 1, a 2 for 2, ..., a Jack for 11, a Queen for 12 and a King for 13. So, it is easier to shuffle cards than mix numbers.
Duration of treatments:
- Perform Pins setting chart (with card games): 5 minutes
- Perform Lugs setting chart: 20 minutes (the first time, but with failure), Further 20 minutes (here with success); In all 40 minutes
- Fill the Forms: about 5 minutes
- Zeroizing the cipher machine: 5 minutes
- Perform Pins setting (on the machine): 8 minutes
- Perform Lugs setting (on the machine): 8 minutes
- Perform 26-letters check: 5 minutes
You can download the forms I used to build an Internal key. You can also download my rough drafts (forms filled)
References
- San Francisco Maritime National Park Assocation
CSP-1500 This page contains a description of the CSP-1500 (The M-209 Navy version), a Navy Key-list and the manual (TM 11-380), 1942 version. - RadioNerds (picture version) TM 11-380, 1942
- iLord.com - M-209 Manual TM 11-380, 1944
- Mark Blair (NF6X) - M-209 Simulator update: generates key-lists
- FM 7-24 Communication in the Infantry Division, 1944
- Crypto-Aids Division. Preparation of OLYMPUS and MARS Keys, 1953. Memorandom to C/SEC, April 8, 1953, NARA N36-10(11), Declassi ed Jan 17, 2012 , E 013526.